Unit 1: Computer Systems
Introduction
Introduction
Introduction to A Level Computer Science.
Teaching Staff - 2024/25
| Component | Year 12 | Year 13 |
|---|---|---|
| Unit 1 | Mr Goulding | Mr Goulding & Mrs Howes |
| Unit 2 | Mrs Howes | Mrs Howes |
| Project | Mrs Howes | Mrs Howes |
Year 12 Topics:
- Topic 1: Structure of the CPU
- Topic 2: CPU Types & IOS
- Topic 3: Operating Systems
- Topic 4: Application Generation
- Topic 5: Software Methodologies
Year 13 Topics:
- Topic 6: Databases
- Topic 7: Networks
- Topic 8: Legislation and issues
- Topic 9: Web Development
- Topic 10: Representing Data
- Topic 11: Boolean logic
Attendance
It is essential that you attend every lesson. If you miss a lesson, your parent must have informed the school and sought approval. Unauthorised absences can lead to staged sanctions which may affect your ability to continue the course. If you miss a lesson, please contact me urgently so that I can help you to catch up. Ultimately, it would be your responsibility to learn what you have missed. However, I would like to help if time permits.
Homework & Revision
You cannot wing an A Level. In addition to attending every lesson, you must complete homework and revision in your own time. This website contains resources that you can access from anywhere. If you need additional help or clarification, please let me know and I will set time aside to help you.
Assessment
After each topic, you will sit a written assessment. This will be marked to see if you are on target. This will also help me to understand any gaps in your knowledge or misconceptions you have adopted. It is important that you revise before each assessment, as you would before the real one.
Year 12 Mock
TBC
Year 13 Final Exams
TBC
Contact information
Mr Goulding is available at bg@range.sefton.sch.uk. Replies will be prompt during school hours. Outside of school hours, responses may be delayed. However, I will attempt to reply as soon as possible.
Topic 1: Structure of the CPU
CPU Components
CPU Components
Topic 1: Structure of the CPU
(1) CPU Components
What does CPU stand for?
Central Processing Unit
What does it mean to ‘process data’?
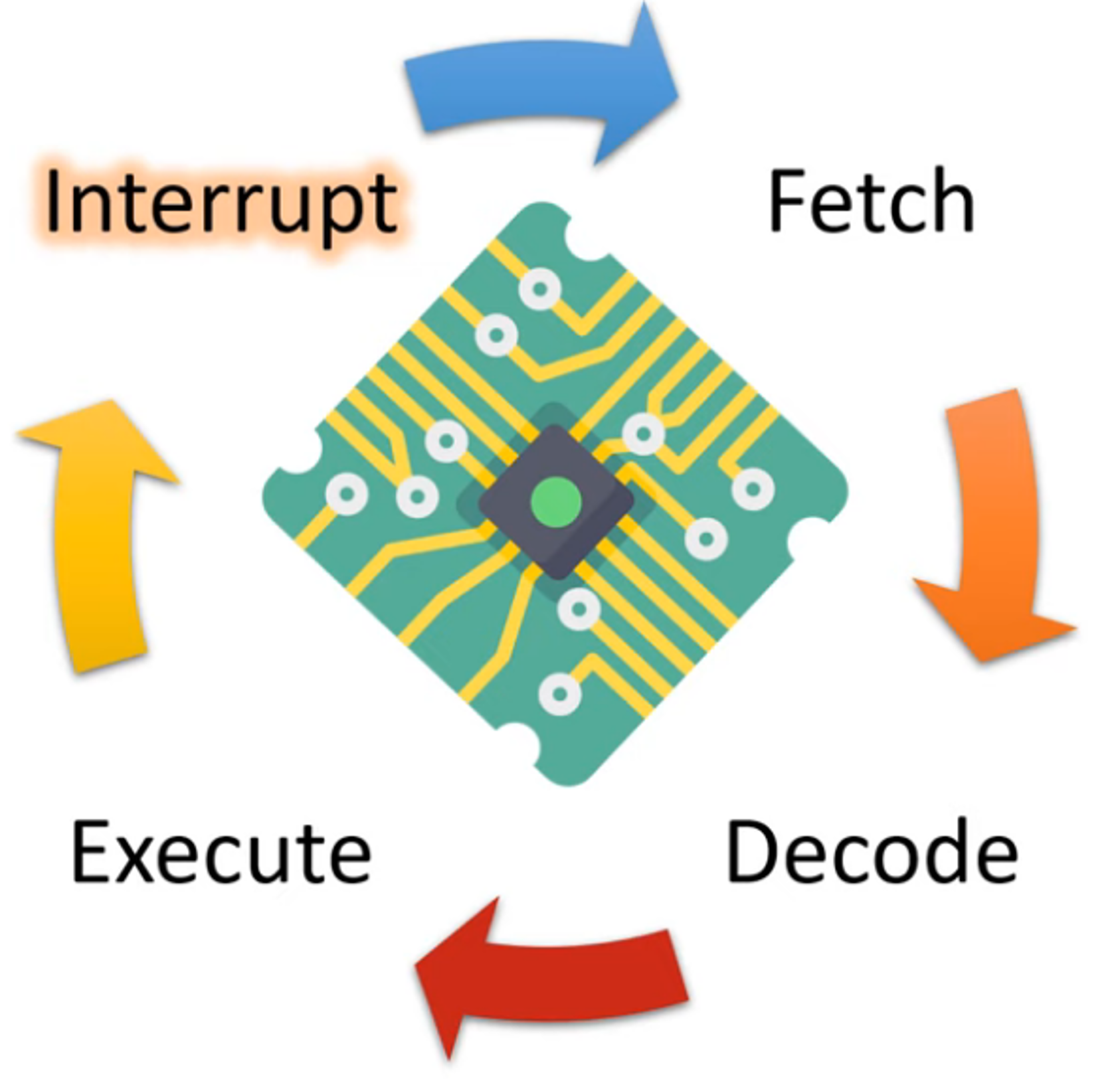
The CPU processes data by completing Fetch, Decode, Execute (FDE) cycles. This diagram represents the FDE cycle:
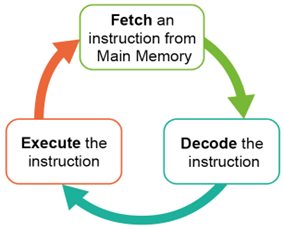
What is meant by Fetch-Decode-Execute?
| Fetch | The instruction/data that needs to be processed needs to be fetched from memory. |
| Decode | Break down the instruction to determine what action is needed. For example, the instruction 0101 means ADD. |
| Execute | Carries out the instruction / action such as carrying out a calculation in the ALU. |
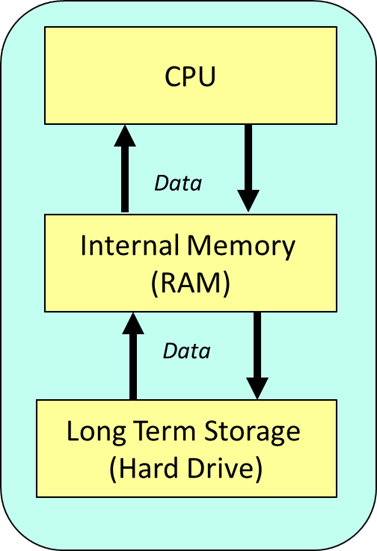
What is the problem with fetching data directly from secondary storage to the CPU?
The hard drive is where all of your files are stored. This is EXTREMELY SLOW. Therefore, it cannot keep up, so the CPU will have to constantly wait for data. Modern CPUs can complete billions of F-D-E cycles per second so secondary storage can’t keep up.
What component is responsible for bringing data from secondary storage to the CPU?
Memory (RAM) is used to speed things up. RAM is faster and will get the data from the hard drive and bring it to the processor quickly. But there can still be some bottlenecks as RAM is still slower than the CPU.
Below is a diagram that represents this process:
There are three sections of the CPU:
| Control Unit (CU) |
| Arithmetic Logic Unit (ALU) |
| Cache |
Control Unit (CU)
The control unit sends control signals that will direct the next operation within the CPU. For example, this could be to start the next FDE cycle.
Examples of tasks performed by the CU include:
| Decoding instructions held in the Current Instruction Register (CIR) |
| the flow of data (bits) between the registers, ALU, memory and other components outside the CPU. |
| Controls the timing of control signals. |
Arithmetic Logic Unit (ALU)
The ALU is part of the CPU that performs arithmetic calculations and logical operations.
Examples include:
| Arithmetic operations such as addition, subtraction, multiplication, division |
| Logical operations such as comparing one data item to another: is it smaller than, greater than or equal to? |
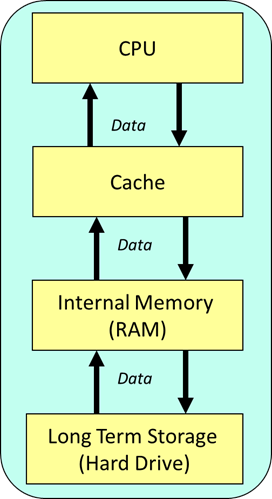
Cache Memory
This is fast memory built into the CPU chip. It will hold frequently used data and instructions so they can be accessed quicker next time rather than having to go back to RAM which is slower than cache. It can help reduce bottlenecks caused by RAM being slow. This is because no matter how fast the clock speed is, RAM will always be a limiting factor.
Why is cache preferred over main memory (RAM)?
Cache memory is built into the same chip as the processor. Unlike the RAM which is a separate component, cache memory is built into the same chip as the processor. Cache can also have prefetching algorithms so it can predict the next likely instruction and fetch this before the CPU requests it.
Here is a diagram that shows the relationship between the CPU, cache, main memory and secondary storage:
What is a bus?
Buses are circuits on the motherboard that connect the CPU to other components such as memory and input/output devices.
What is the System Bus?
A system bus is a general term that is used to refer to all three buses: Data Bus, Address Bus and Control Bus.
Here is a diagram that shows the relationship between all three buses:
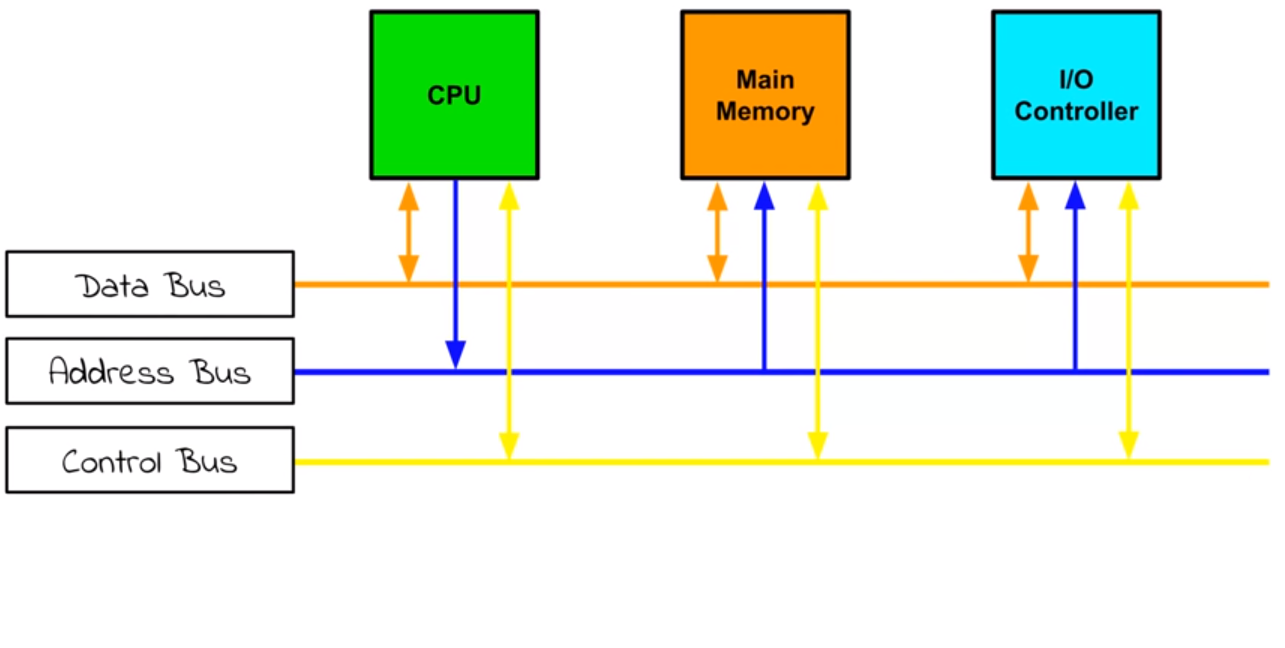
The I/O refers to keyboards, mice and the hard drive.
| Bus | Description |
|---|---|
| Data bus | Transmits data or instructions between the CPU-memory and CPU-I/O. This is a bi-directional bus. This means the bits (1s and 0s) can be carried both ways. |
| Address bus | Transmits the memory address of where data is about to be fetched from or written to. This is a single directional bus from the CPU to memory. |
| Control bus | Transmits control signals between the CPU-memory and CPU-I/O. This allows the control unit to control and coordinate the activities within the computer. It is a bi-directional bus. |
Craig N Dave video
FDE Cycle
FDE Cycle
Topic 1: Structure of the CPU
(2) FDE Cycle
What is a register?
A small piece of fast memory built into the CPU. Registers are used for a particular purpose during the FDE cycle. Registers temporarily store one piece of data at a time. Registers are sometimes called ‘special registers’.
The table below contains five common registers that are used during the FDE cycle. There are more registers that we will learn about later but, for now, these are the ones you need to know.
| Register | Role |
|---|---|
| Program Counter (PC) | A register that holds the address of the next instruction to be fetched, decoded and executed. After sending the value, the PC is incremented by 1. The value in the PC may change if there is a branch instruction from the CIR. |
| Memory Address Register (MAR) | A register that holds the memory address of where data is about to be fetched from or written to. This value is carried from the CPU to memory using the address bus. |
| Memory Data Register (MDR) | A register that holds the instruction or data fetched from or written to memory. This is carried along the data bus between the CPU-memory. |
| Current Instruction Register (CIR) |
A register in the CPU that stores the instruction currently being decoded and executed by the CPU. Instructions are split into two parts:
|
| Accumulator (ACC) | The Accumulator TEMPORARILY stores the immediate results of calculations from the ALU. The Accumulator also acts as a buffer/gateway for all of the inputs and outputs of the CPU |
The FDE cycle
The FDE cycle is explained below. This explanation does NOT detail how 'interrupts' are carried out. This is also important and we will learn about this in a future topic.
Fetch Stage 1
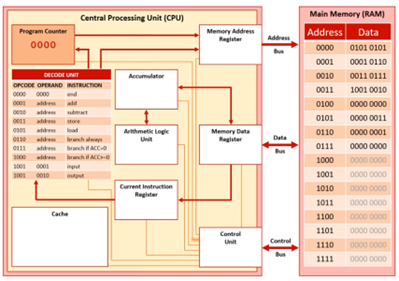
The PC is checked because it holds the address of the next instruction. In this case, the address is 0000.
Fetch Stage 2
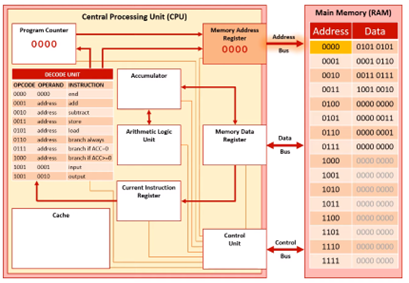
The address from the PC (0000) is copied to the MAR. The address then travels along the address bus from the CPU to memory where it waits to receive a signal from the control unit.
Fetch Stage 3
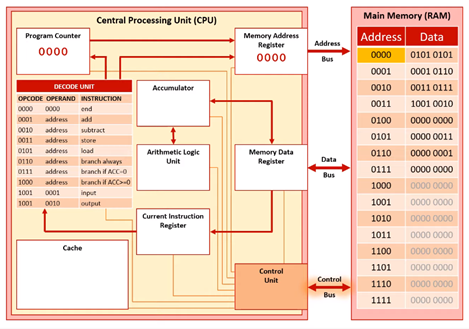
The control unit sends a read signal. This travels along the control bus to memory.
Fetch Stage 4
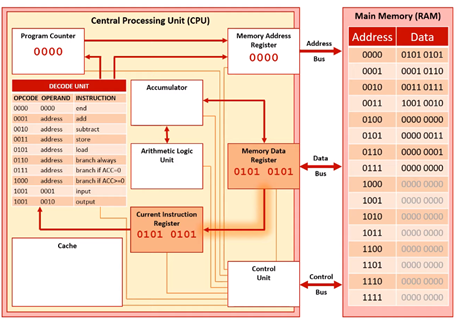
The contents stored in the memory address 0000 are sent along the data bus to MDR 0101 0101. This is then copied to the CIR.
Fetch Stage 5
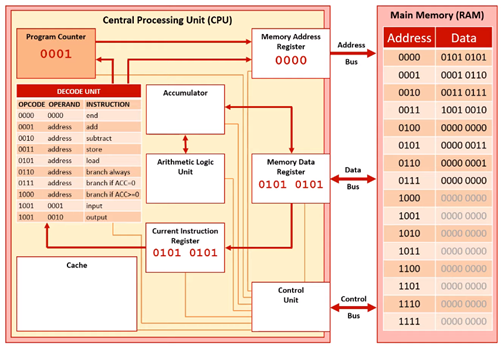
The instruction has now been fetched from memory. The PC is now incremented by one, so it points to the address of the next instruction to be executed.
Decode Stage 1
The instruction that is held in the CIR is now ready to be decoded.
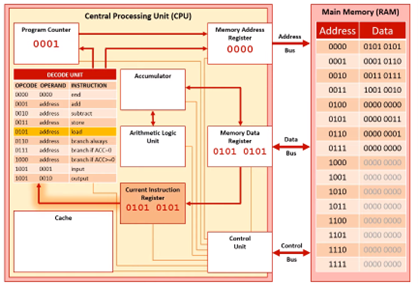
Decode Stage 2
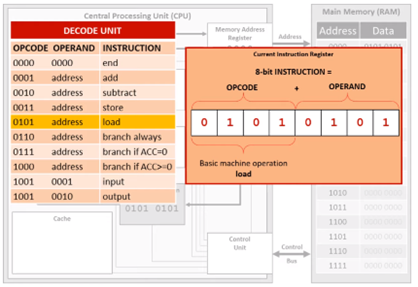
The OPCODE (action) and OPERAND (data) are examined. Here the OPCODE is LOAD and the OPERAND is 0101. This means we need to load the contents of memory address 0101 to the accumulator.
Don't panic: you do NOT need to learn what the binary codes mean.
Execute Stage 1
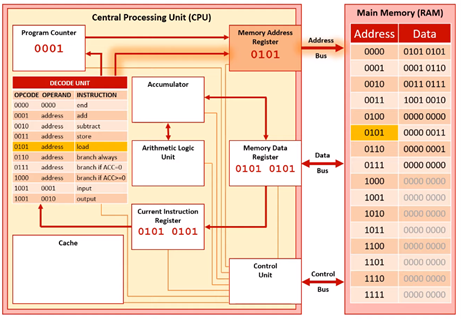
We send memory address 0101 to the MAR. This is then sent down the address bus to memory.
Execute Stage 2
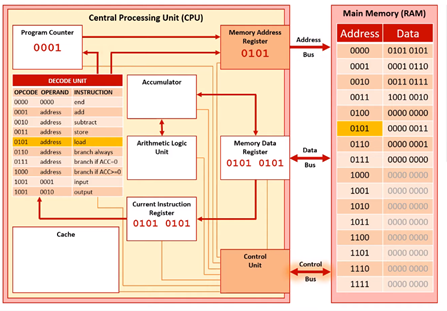
The control unit sends a read signal along the control bus to main memory.
Execute Stage 3
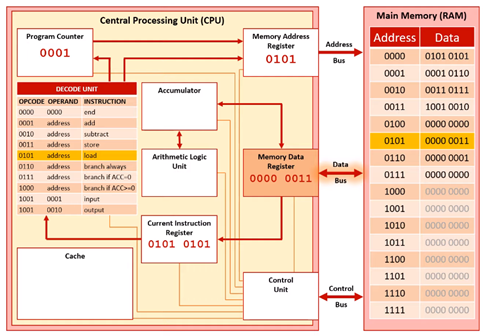
The contents of memory location 0101 are then sent along the data bus to the MDR (000 0011).
Execute Stage 4
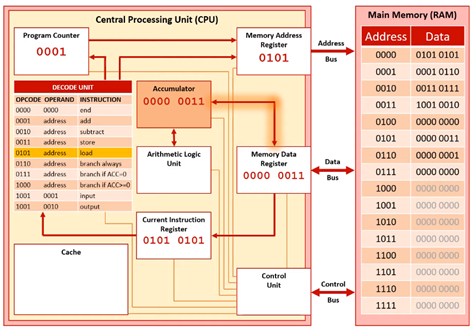
The contents are then copied into the accumulator.
Craig N Dave video
CPU Performance
CPU Performance
Topic 1: Structure of the CPU
(3) CPU Performance
What factors impact the performance of the CPU?
| Clock speed |
| Number of cores |
| Cache size |
What is meant by 'clock speed'?
This is how many times the CPU can carry out the Fetch-Decode-Execute cycle PER SECOND. It is measured in Hertz (Hz).
Units used to measure clock speed
| 1 Hz (Hertz) |
| 1 kHz (Kilohertz) |
| 1 MHz (Megahertz) |
| 1 GHz (Gigahertz) |
For each unit, how many instructions can be fetched, decoded and executed per second?
| 1 Hertz | 1 FDE cycle per second |
| 1 Kilohertz | 1,000 FDE cycles per second |
| 1 Megahertz | 1,000,000 FDE cycles per second |
| 1 Gigahertz | 1,000,000,000 FDE cycles per second |
Why does increasing the clock speed increase CPU performance?
By increasing the clock speed, it will mean that the CPU can do more Fetch-Decode-Execute cycles per second. This will mean that the CPU performance will improve.
What is meant by the term 'overclocking'?
It is possible to change the clock speed in the computer BIOS to try to make their computer run faster. This is called overclocking. If the clock speed is too fast, the processing will not be completed before the next instruction is carried out. If the CPU cannot keep up with the pace of the clock, the data is corrupted. CPUs can also overheat if they are forced to work faster than they were designed to work.
What is meant by the term 'core' and what does each core do at the same time?
A core is a processing unit. One CPU can have several cores. Each core will have its own ALU and Control unit. This means that it can Fetch-Decode-Execute several things at the SAME TIME.
How does increasing the number of cores increase CPU performance?
By increasing the number of cores, it will mean that the CPU can do more Fetch-Decode-Execute cycles AT THE SAME TIME. This will therefore mean that the CPU performance will improve.
How many instructions can each core perform?
| Type | No. of cores | No. of FDE at once |
|---|---|---|
| Single | 1 core | 1 FDE cycle at once |
| Dual | 2 cores | 2 FDE cycles at once |
| Quad | 4 cores | 4 FDE cycles at once |
| Hex | 6 cores | 6 FDE cycles at once |
How does more cache memory increase performance of the CPU?
The more cache the more ‘regularly’ processed data can be held by the CPU, therefore ensuring that the CPU does not have to wait for these instructions to be brought from memory.
The following processors are ranked from best to worst.
| CPU 1 | CPU 2 | CPU 3 | CPU 4 | |
|---|---|---|---|---|
| Clock speed | 3.6GHz | 4.6MHz | 3.2GHz | 2.7GHz |
| No. of cores | 4 | 1 | 2 | 4 |
| Cache size | 8MB | - | 3MB | 4MB |
| 1. Processor 1 |
| 2. Processor 4 |
| 3. Processor 3 |
| 4. Processor 2 |
Which of the above processors has the best performance and why?
Processor 1 has 4 cores which can process data independently across four different cores. It also has the largest cache memory so can hold more regularly processed data and instructions reducing the bottlenecks caused by waiting for data and instructions to be fetched from RAM.
Why would processor 4 give better performance than processor 3?
Although processor 4 has a smaller clock speed than processor 3, it has double the amount of cores so can complete more FDE cycles at the same time and more cache memory.
Craig N Dave video
Pipelining
Pipelining
Topic 1: Structure of the CPU
(4) Pipelining
What is meant by the term 'pipelining'?
Pipelining makes more efficient use of the CPU because multiple instructions are processed concurrently. This is because as one instruction is being executed, another is being decoded and another is being fetched at the same time. This increases the speed of execution and increases the performance of the CPU because more instructions can be carried out in the same amount of time.
This table represents how pipelining works:
| Fetch | Decode | Execute | |
|---|---|---|---|
| Step one | Instruction 1 | ||
| Step two | Instruction 2 | Instruction 1 | |
| Step three | Instruction 3 | Instruction 2 | Instruction 1 |
| Step four | Instruction 4 | Instruction 3 | Instruction 2 |
| Step five | Instruction 5 | Instruction 4 | Instruction 3 |
Explanation of step 3 in the table above
Instruction 1 is actually being executed. However, at the same time, instruction 2 is being decoded and at the same time instruction 3 is being fetched from memory.
Example in Python code
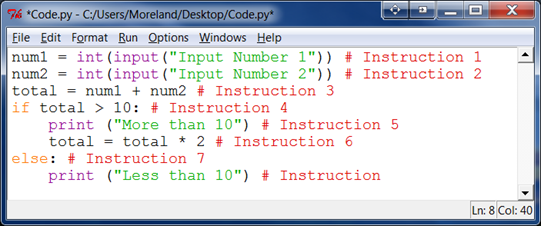
You should assume that the value inputted for variable num1 is 2 and the value inputted for variable num2 is 3.
Using the table below, show how pipelining can used in the above programming code. You may notice a problem with pipelining at some point.
| Fetch | Decode | Execute | |
|---|---|---|---|
| Step one | Instruction 1 | ||
| Step two | Instruction 2 | Instruction 1 | |
| Step three | Instruction 3 | Instruction 2 | Instruction 1 |
| Step four | Instruction 4 | Instruction 3 | Instruction 2 |
| Step five | Instruction 5 | Instruction 4 | Instruction 3 |
| Step six | Instruction 6 | Instruction 5 | Instruction 4 |
In the example above, Instructions 6 and 5 would need to be flushed at Step Six.
What is meant by the term 'flush' and why is it needed?
Flushing will clear the pipeline of all of the instructions that are already in the pipeline - being fetched, decoded, or waiting to be executed.>
In the example above, when instruction 4 has been executed then this means that the program will need to jump to instruction 7 (as the value in the variable is less than 10.) However instruction 5 and 6 are in the pipe to be executed next. Therefore, these need to be flushed to fetch and decode instruction 7.
What are the benefits and drawbacks of pipelining?
| Benefits | Drawbacks |
|---|---|
| Multiple instructions can be processed concurrently. | Not efficient if there are lots of JUMP instructions which increases the amount of flushing that has to occur. This is because there will be lots of instructions backed up in the pipeline that will no longer be the next ones to be executed. The more flushing that occurs reduces the benefits of pipelining. |
| Increased throughput - more instructions can be completed in the same amount of time. | Data hazards can occur. This means that an instruction can attempt to access/use data before the data is available. This is because it is not always easy to predict what instruction needs to be fetched and decoded next. |
Craig n Dave video
CPU Architecture
CPU Architecture
Topic 1: Structure of the CPU
(5) CPU Architecture
What is a CPU architecture?
This is the arrangement/layout of the electronic components in and around the CPU. For example:
- ALU
- Control unit
- Registers
- Memory
- Buses
Two common architectures are Von Neumann Architecture and Harvard Architecture.
What is meant by the term Von Neumann Architecture?
This has ONE SINGLE memory unit that stores data AND instructions together in the same format. It uses the same bus for data and instructions. It has a single control unit and a single ALU. Instructions are executed sequentially and it can only fetch either data or instructions at one time.
This diagram represents the setup of Von Neumann Architecture:
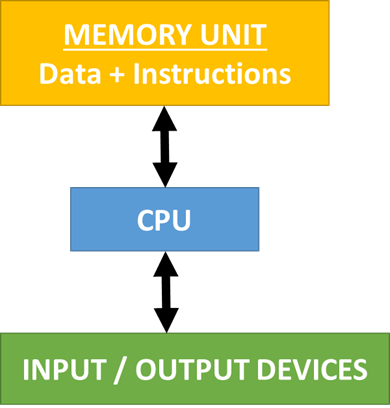
What are the benefits and drawbacks of Von Neumann Architecture?
| Benefits | Drawbacks |
|---|---|
| Single memory unit for data and instructions simplifies the design. | Only one bus is used. This means the CPU is idle waiting for instructions/data. |
| Manufacturing this architecture is cheaper | Parallel executions of programs are not allowed due to serial instruction processing. |
| Data/instructions are in the same format in the same memory unit. |
How may modern contemporary CPU architectures differ from pure Von Neumann architecture?
Contemporary processors have performance enhancing features to give better performance. For example:
| Two separate areas of memory - One for instructions & one for data allowing for instructions and data can be accessed concurrently. |
| Pipelining - Whilst an instruction is being executed the next can be decoded and the subsequent one fetched. |
| Use of Cache - A small amount of high performance memory (next to the CPU) which stores frequently used data/instructions. |
| Multiple Cores - Each core acts as a separate processing unit. |
| Virtual cores - Treating a physical core as two virtual cores. |
| On-board Graphics - Built in circuitry for graphics processing to take the strain off the CPU. |
What is meant by the term Harvard Architecture?
An adapted version of Von Neumann architecture. It has TWO SEPARATE memory units that store data and instructions separately. It uses different data and address buses for data and instructions. It has a single control unit and a single ALU.
Below is a diagram that represents the setup of Harvard Architecture:
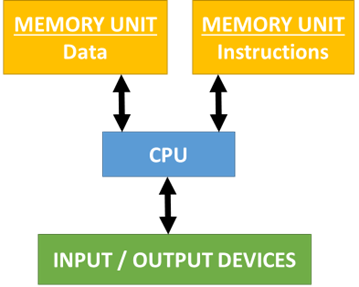
What are the benefits and drawbacks of Harvard Architecture?
| Benefits | Drawbacks |
|---|---|
| Faster processing as instructions and data can be simultaneously fetched. | More complex design (e.g. two buses, motherboard for doubling memory) |
| Less chance of data corruption as data/ instructions are held in separate memory units. | Manufacturing this architecture is more expensive. |
| You could run out of one memory (e.g. instructions) with unused memory in the other memory unit (e.g. data). |
Von Neumann v. Harvard Architecture
| Von Neumann | Harvard |
|---|---|
| One memory unit for data and instructions to be stored in the same format | Two separate memory units: one for data, one for instructions. |
| One data bus | Two data buses |
| Less complex architecture, making it cheaper to manufacture. | More complex architecture, making it more expensive to manufacture. |
| 1 data bus means data can't be fetched at the same time as an instrucrtion. | 2 data buses means that data and instructions can be fetched simulatenously. |
Craig n Dave video
Topic 2: CPU Types & IOS
CISC & RISC
CISC & RISC
Topic 2: CPU Types & IOS
(1) CISC & RISC
What is an instruction set?
This is a list of all instructions that can be recognised and executed by the CPU. Two types include CISC and RISC.
When would you use a CISC instruction set?
CISC is designed to complete a task in as few lines of (assembly) code as possible at higher speeds. It is used in general purpose computers (desktop PCs and laptops).
When would you use a RISC instruction set?
RISC is designed to perform instructions in an efficient way. It is used in portable devices (e.g. phones, smart watches) and embedded systems.
Key differences between CISC and RISC
| CISC | RISC | |
|---|---|---|
| What does it stand for? | Complex Instruction Set | Reduced Instruction Set |
| Example Code | MULT 0000, 0001 | LDA 0000, 0000 LDA 0001, 0001 PROD 0000 0001 STA 0010 0000 |
| Type of instructions | Complex Instructions. The length of the programming code is short. | Simple Instructions. The length of the programming code is long. |
| Number of instructions | Has a larger set of instructions of variable length. Some instructions in CISC will rarely get used. | Has a smaller set of instructions of fixed length. Instructions are used regularly. |
| Hardware or software emphasis | Focuses on hardware. The processor (hardware) has to be more complex and has to do more work. | Focuses on software. The compiler (software) needs to be more complex and has to do more work. |
| Number of clock cycles | Takes multiple clock cycles to execute an instruction. | Takes one clock cycle to execute instructions. |
| Hardware requirements | Requires more complex hardware which requires cooling. Devices tend to be more bulky. | Requires less complex hardware and therefore little / no cooling. Devices tend to be lighter and more portable. |
| Power usage | Greater energy consumption to power complex hardware and cooling mechanisms. Not ideal for battery operated devices. | Lower energy consumption as there is less hardware to power and little/no cooling. Ideal for battery devices. |
| Number of CPU registers | Fewer CPU registers. | More CPU registers |
| Memory efficiency | Makes more efficient use of memory. | Makes inefficient use of memory. |
| Pipelining | Can’t make use of pipelining | Can support pipelining. Instructions are smaller. |
| Cost | Costs more to design/manufacture as it has complex circuitry. | Costs less to design/produce. There is little cooling, smaller battery and a simpler circuit. |
Craig n Dave video
Downloads
Multicore v Parallel
Multicore v Parallel
Topic 2: CPU Types & IOS
(2) Multicore v Parallel
What is meant by the term 'multicore processor'?
A single chip containing two or more independent processing units. Each unit/core will fetch-decode-execute its own set of instructions at the exact same time as another unit/core. Each core has its control unit, ALU and set of registers.
Examples of multicore processors
- Dual Core - 2 independent processing units
- Quad Core - 4 independent processing units
- Hexa Core - 6 independent processing units
How can the performance of processes that use multiple cores be further enhanced?
- The different cores are able to communicate with each other
- Each core can have shared access to the cache memory
What is a key benefit and drawback of multicore processing?
| Benefit | Drawback |
|---|---|
| Several tasks can be performed simultaneously which increases the performance. | There are some overheads associated with using more than one processor/core. |
What is meant by the term 'parallel processor'?
This is when parts of an instruction are divided between multiple cores to be carried out at the same time. Each core can process part of a task.
How is parallel processing used in this example?
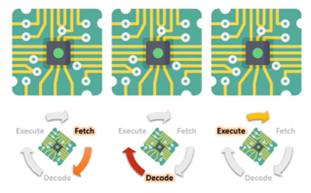
- One core/unit is fetching a new instruction
- A separate unit/core is decoding the previous instruction
- Another unit/core is executing the instruction before that
How is parallel processing used in this example?
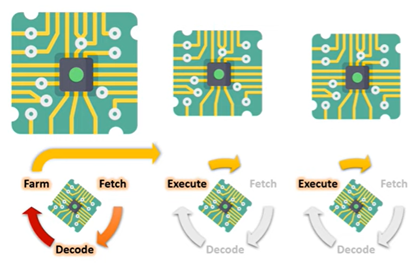
- One core/unit is fetching and decoding an instruction.
- It will farm off the various parts of the program to other processing cores/units to be executed.
NOTE: Parallel processing is an example of how pipelining can be implemented in practice.
What are the benefits and drawbacks of parallel processing?
| Benefits | Drawbacks |
|---|---|
| Several tasks can be performed simultaneously. This can increase the speed of processing (e.g. repetitive calculations on large data sets). | There is an overhead in coordinating the processors and some tasks may run faster with a single processor than multiple processors. |
| Huge performance increase for graphics processing (e.g. 3D graphics). | Not all problems are parallelisable. X processors does not mean it will run in 1/xth of the time of one processor. |
Why doesn't doubling the number of cores double performance?
- Some instructions may not be able to run across multiple cores.
- Some programs can’t make maximum use of all cores or they are not designed to. Programs (including the OS) have to be designed to specifically use multiple cores.
- Sometimes an instruction in one core may be waiting for another instruction to be completed.
- Other factors can influence the processing speed such as clock speed, cache size, bottle necks etc. The clock speeds is generally the most important factor in determining the CPU performance.
- There are overhead costs. Sometimes the different cores have to communicate with each other through channels which takes away some of the speed.
Craig n Dave video
GPUs
GPUs
Topic 2: CPU Types & IOS
(3) GPUs
What is a co-processor?
An additional processor that is used concurrently alongside the main CPU to complete specialised tasks. Its aim is to improve the overall speed of the computer and take the strain away from the central processing unit.
A GPU is a well-known co-processor. What does GPU stand for?
Graphics Processing Unit.
Difference between a CPU and a GPU
A CPU is a general purpose processing unit. A GPU is highly specialised to perform calculations associated with graphics.
What type of instructions do CPUs and GPUs work best on?
- CPUs perform well on complex operations on small datasets.
- GPUs perform well on simple operations on large datasets. GPUs work well because they can apply the same simple operation to large datasets at one time.
GPUs are capable of Single Instruction Multiple Data (SIMD). What does this mean?
SIMD means that one instruction operates on multiple pieces of data simulatenously. This makes GPUs ideal for applying the same instruction to a large dataset at the same time.
Why are GPUs ideal for processing graphics such as video games or simulations?
GPUs are ideal for graphics because they are specialised to perform this task. GPUs often have built in circuitry and instructions for common graphics operations. GPUs are able to perform a single instruction on multiple pieces of data at one time (SIMD). Often we want to do this when processing graphics. For example, when transforming points on a polygon or shading pixels.
Looking at this photo. What would be involved in rendering this 3D image of a mountain landscape in full colour with realistic lighting?
- Each segment of the image would be assigned XYZ coordinates.
- Each segment would be assigned a texture or pattern (RGB colour).
- A light source would be assigned and given an angle and brightness.
These simple instructions will need to be repeated for every pixel. This is an example of Single Instruction Multiple Data (SIMD) instructions in practice.
Can GPUs make use of parallel processing?
Yes – GPUs are able to perform a single instruction on multiple pieces of data at the same time. It can process calculations in parallel. For example, the calculations on one pixel in an image will not affect another pixel so multiple calculations can take place at once.
Can GPUs be used to process non-graphical data?
Yes – GPUs can be used for operations other than rendering graphics. This is because any situation that requires processing of thousands or even millions of simple calculations on a large dataset (Single Instruction Multiple Data) can be done more efficiently using a GPU.
Examples of non-graphical data that a GPU may process
- Performing complex numerical calculations
- Running modelling software:
- Weather modelling
- Statistical analysis
- Stock level predictions
- Data mining - analysing millions of pieces of data to look for trends/patterns.
- Calculations on matrices, vectors, multiple data at the same time. For example, insurance pricing, modelling risk, calculating bills
- Breaking passwords
- Machine learning
Craig n Dave video
Input & Output
Input & Output
Topic 2: CPU Types & IOS
(4) Input & Output
Diagram showing relationship between input, process, output

Input devices
| Input device | Description |
|---|---|
| Keyboard | Used to enter text such as letters, numbers and punctuation. |
| Mouse | Used to select options on the screen using a pointer. |
| Touch screen | Allows the user to select options on the screen with their finger. This is known as a hybrid device as it is an input and output device in one. |
| Webcam | This is used to enter live images of something usually a person when in a video call. |
| QR Reader | This is used to read data that has been stored as an image. They are often used to contain links to websites. |
| Biometric Reader | This will read biometrics from the user such as finger print recognition, voice recognition, facial recognition etc. |
| Scanners | Used to convert a physical document to a digital document so that it can be edited. |
| Sensor | Used to collect data about the environment. Examples include noise, light, temperature and moisture. |
| Barcode reader | Used to scan/read a barcode and then convert it to a number which can then be used to lookup the item in a database. |
| Games controller | Used to input commands into a computer game such as the direction the player should move. |
| Microphone | Used to capture audio so that it can be used by a computer program. Often used when making a voice/video call. It can also be used with speech-to-text recognition software. |
| Graphics tablet | Allows the user to create freehand drawings. |
| Optical Character Recognition (OCR) | This will scan an image and then convert any kind of written text that has been typed, handwritten or printed into machine-readable text. It will transfer this text into a word processor so it can be edited. |
| Optical Mark Recognition (OMR) | This will detect markings in a pre-defined area. For example on a questionnaire, it can detect if a box has been ticked or not. |
Output devices
| Output device | Description |
|---|---|
| Monitor | Used to display graphical information on a screen. This is what the user will see (the user interface) and it allows them to actually interact with their device. |
| Printer | A device that is used to create a physical copy of a digital document. Types include inkjet printers and laser printers. |
| Speaker / headphones | Used to output sound such as music or error sounds. |
| Projector | Used to display the contents of a monitor onto a large screen or wall. |
Craig n Dave video
Storage Devices
Storage Devices
Topic 2: CPU Types & IOS
(5) Storage Devices
What is the difference between memory and storage?
| Memory | Storage |
|---|---|
| Provides very fast temporary storage for active data/programs for the CPU. | Provides permanent storage of vast amounts of data. |
| This is storage that has direct contact with the CPU. | This is storage that DOES NOT have direct contact with the CPU. |
| The data is not saved when the power is turned off. It is volatile storage. | The data is saved when the power is turned off. It is non-volatile storage. |
What are three types of secondary storage?
- Optical
- Magnetic
- Flash (solid state)
Examples of optical storage
- CDs - max capacity around 700MB
- DVDs - max capacity around 4.7GB
- Blu-Rays - max capacity around 25GB
Each type of optical storage has an R verison (CD-R, DVD-R, BD-R) and an RW version (CD-RW, DVD-RW and BD-RW). What is the difference?
- CD-R, DVD-R and BD-R can be written to once. This means that when you have written data to the disc, it can only be read from that point on.
- CD-RW, DVD-RW and BD-RW can be written to many times. This means that once you have written the data to the disc, you can read the data from the disc but also erase the data and reuse it.
How does optical storage work?
- Optical discs are made up of CDs, DVDs and Blu-Rays.
- Optical discs contain tiny pits and lands, which are too small to be seen by the human eye.
- Data (binary) is burnt into the pits and lands into a spiral track circulating outwards from the centre
- To read the data from an optical disc, a laser beam passes over the pits and lands. As the laser beam passes over them, light will be reflected back.
- From this signal, 0s and 1s can be derived from reflections or no reflections
Benefits and drawbacks of optical storage
| Benefits | Drawbacks |
|---|---|
| Individual discs are cheap to buy. However, it could get expensive if you need many discs. | They are not very robust as the discs can easily get scratched so data cannot be read. |
| They are very portable as the discs can easily be moved around. | The amount of storage capacity is small. |
| They have very slow read and write speeds. |
Examples of magnetic storage
- Hard drives - max capacity around 1-4TB
- Floppy discs - max capacity around 1.44MB
How does magnetic storage work?
- Magnetic storage is made up from a platter (the circular disc that spins.)
- The platter is split into circles called tracks and each track is divided into sectors.
- Data is stored into the sectors by magnetising the sectors.
- Disk heads mounted on mechanical arms can therefore read the magnetised data stored in the sectors.
Benefits and drawbacks of magnetic storage
| Benefits | Drawbacks |
|---|---|
| They are very cheap to buy. You can buy lots of storage for a low price. | They are not very portable. They often tend to be heavy and are often built into computers. They need to be larger so there is space for the moving parts. |
| They offer a high storage capacity. | They are not robust as they contain lots of moving parts that be damaged if dropped. e.g. the read-write head could come into contact with the platter if dropped. |
| They have fast read / write speeds. |
Examples of flash storage
- Solid state drive - up to 4TB
- Memory sticks - up to 32GB
- SD card - up to 128GB
How does flash storage work?
- Flash storage disks use non-volatile flash memory to store information.
- This is made of microchips (switches)
- Data is stored on the microchips by changing the state of the switches.
- The state of the switches determine if a 1 or 0 is stored.
Benefits and drawbacks of flash storage
| Benefits | Drawbacks |
|---|---|
| They are very robust as they do not contain moving parts that can be damaged if dropped. | They are very expensive to buy. |
| They offer a high storage capacity (although not as much as magnetic). | The cost of flash storage per GB is considerably higher than magnetic. This means you can get a higher storage capacity with magnetic for the same price as flash. |
| They have very fast read / write speeds as there are no moving parts. | |
| They are very portable and lightweight. This is because storage devices with no moving parts take up less space. Storage devices with moving parts need more space so the parts can move. |
Craig n Dave video
ROM & RAM
ROM & RAM
Topic 2: CPU Types & IOS
(6) ROM & RAM
What does RAM stand for?
Random Access Memory
What does RAM hold?
Active data and programs. This is so the CPU can access them quickly.
What data unit is RAM often measured in?
Often measured in Gigabytes (GB)
RAM is volatile memory. What does this mean?
Volatile means that when the computer is turned OFF then anything stored in RAM is lost. This is why you will lose your work if you turn your computer off without saving to secondary storage which is non-volatile.
Why does having more RAM increase the computer's performance?
The CPU accesses data/programs from RAM because it is faster than accessing the data from secondary storage. Therefore, the more RAM you have, the more active data/ programs can be held and accessed quickly by the CPU. If RAM is full, the computer will need to make use of virtual memory (see next lesson) which is a lot slower. Therefore the more RAM you have the less chances there is that the computer will need to use virtual memory.
What does ROM stand for?
Read Only Memory
What does ROM hold?
ROM holds the instructions that are used to start up the computer (BIOS) and device settings such as overclocking.
What data unit is ROM measured in?
Often measured in Megabytes (MB)
ROM is non-volatile memory. What does this mean?
Non-volatile means that when the computer is turned OFF then anything stored in ROM is NOT lost.
The start-up instructions for the computer (BIOS) are stored in the ROM. Explain the steps that are followed when the computer is switched on.
- Computer is turned on.
- BIOS is loaded from ROM into RAM.
- Checks components are availabe and working via POST checks (Power On Self Test).
- Finds the operating system, loads it into main memory and passes control over to it.
This is a diagram that shows the same:
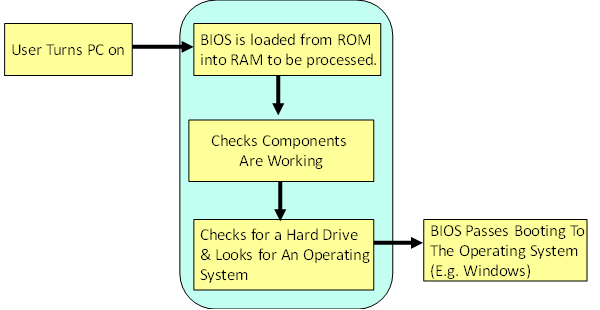
Why is BIOS stored in ROM, not RAM?
RAM is volatile so the BIOS would be lost when the computer turns off. When the computer is turned on, the computer would not have the start-up instructions to boot or carry out hardware checks. This would make the computer unusable. ROM is non-volatile so the data is not lost when the computer turns off. This means that the start-up instructions will be available when the computer is switched back on.
Comparison table for ROM and RAM
| RAM | ROM | |
|---|---|---|
| Does it store data? | Yes | Yes |
| What does it stand for? | Random Access Memory | Read Only Memory |
| What is it used for? | Active programs & Active data | BIOS & device settings |
| Volatile or non-volatile? | Volatile | Non-volatile |
| Read/write data to it? | You can read / write data. | You can ONLY read data. |
Craig n Dave video
Virtual Data
Virtual Data
Topic 2: CPU Types & IOS
(7) ROM & RAM
What is meant by the term 'virtual memory'?
Virtual memory is for when the RAM is full. It is a pre-determined area of secondary storage called a page file that is used for active data/programs. Currently unneeded data/programs are stored in virtual memory. It is volatile so any data stored will be removed once the device is turned off. If something in virtual memory is needed, we must swapped it for something memory before it is transferred to the CPU.
Virtual memory is volatile. This means that the data is lost when the PC is turned off.
Why is virtual memory slow?
Virtual memory is slow because it doesn’t have direct contact with the CPU. If we want to use something in virtual memory, it must be swapped with something in the main memory before being transferred to the CPU.
Example of virtual memory
Below is an image of RAM and Virtual Memory. The presentation software is stored in virtual memory because it won't fit into RAM.
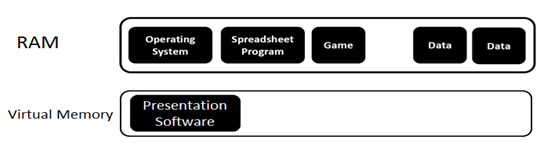
If the presentation software needs to be used, something will need to be swapped from RAM to virtual storage to make room for it. The diagram below shows this process:
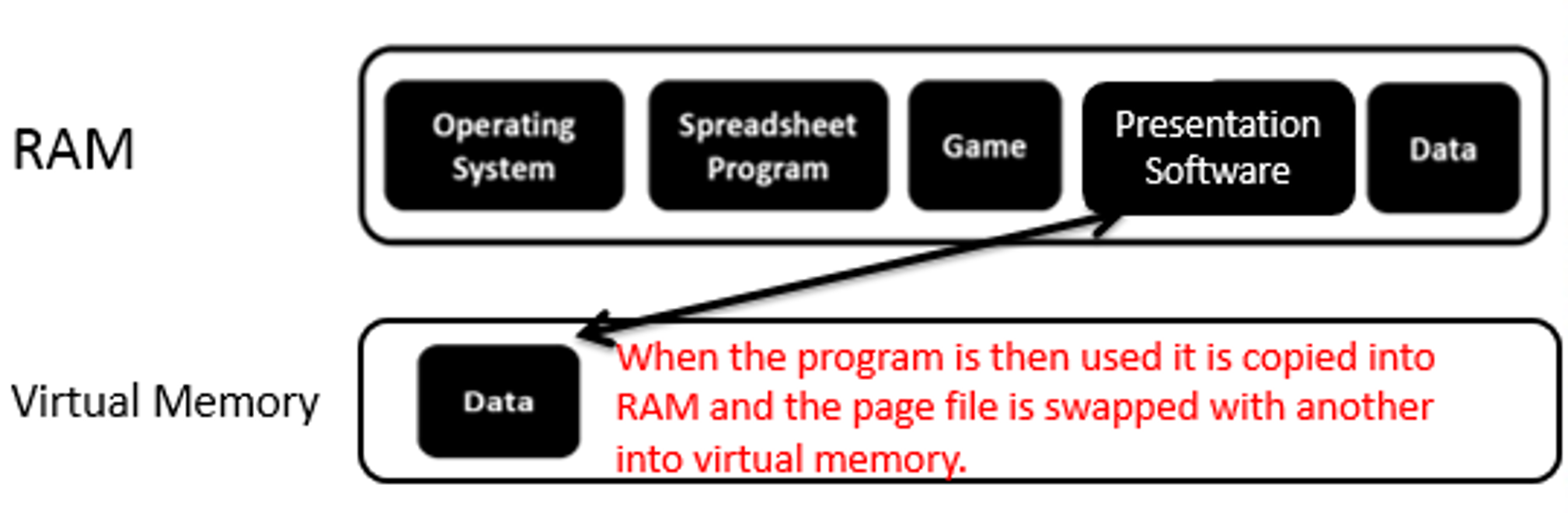
What is virtual storage?
This is when data is not stored locally on the computer that the user is using. Instead data is stored remotely (virtually) in another location.
Remember, all virtual storage is data that is stored physically on a device somewhere. Name some places where virtual storage may be saved.
- On another computer/server/device in the same network
- Remotely on a device in another network.
- In the cloud.
What are the benefits and drawbacks of virtual storage?
| Benefits | Drawbacks |
|---|---|
| The data stored can usually be stored on different devices in different locations.This means it can be accessed from anywhere and the data will not be lost if there is a disaster on site. | You often need an internet connection if you are storing data in the cloud or another network. |
| You can use storage flexibly. Storage can be expanded as needed. Additionally, computers with a small amount of internal storage will not be limited because files can be stored remotely | More data transfer between computers increases the risk of security threats. |
| Data storage can be more centralised which makes backups easier. | The device where the data is stored has to be available. |
| No onsite maintenance is needed for virtual storage. | |
| No physical space is needed locally for backups of data kept on site. |
Craig n Dave video
Topic 3: Operating Systems
Operating Systems
Operating Systems
Topic 3: Operating systems
(1) Operating systems
What is an operating system?
This allows the user to interact with the hardware. It controls the hardware and software of a computer system and provides a user interface to allow the user to use and input commands to the hardware.
What are the functions of an operating system?
- Memory/Resource management
- File management
- Security management / controlling access handling
- Interrupt handling
- Providing a platform for other software
- Providing a user interface (UI)
- Providing utilities for system maintenance
- Controlling hardware / peripheral devices
| Function | Description |
|---|---|
| File management | Storing files in secondary storage, searching for files and folders, copying, moving and renaming files and folders. |
| Memory/resource management | Allows data to be moved from secondary storage to main memory, and between virtual memory and memory. Ensures that RAM is used efficiently and is not wasted. Data that is not needed anymore is removed (garbage collection). Space is freed up and allocated to data/programs that need it. Data is kept secure by not allowing programs to access memory reserved for another program. This allows more than one program to run at the same time (multitasking). |
| Security management / controlling access | Controlling who can access the computer system. Controlling who can access certain resources on the computer system. |
| Providing a platform for other software | Allows additional software to be installed on the computer such as application software that will allow the user to complete additional tasks. |
| Providing a user interface | This allows the user to interact with the hardware and software. This is often through the use of windows, icons, menus and pointers (WIMP). |
| Provides utilities for system maintenance | Provides application software that performs one or more tasks. Used to monitor, manage and maintain the system. For example, file repair, backup, compression and defragmentation. |
| Interrupt handling | Stops the current FDE cycle to handle a request from another device or process that requires the immediate attention of the CPU. For example, antivirus has detected a threat. |
| Controlling hardware / peripheral devices | It uses device drivers to tell the operating system how to communicate with a peripheral device. It will translate operating system instructions into a series of instructions that the specific piece of hardware can understand. It also controls hardware such as the GPU. |
Craig n Dave video
Memory Management
Memory Management
Topic 3: Operating systems
(2) Memory management
Here is some RAM. It is currently holding four active programs called A, B, C and D.
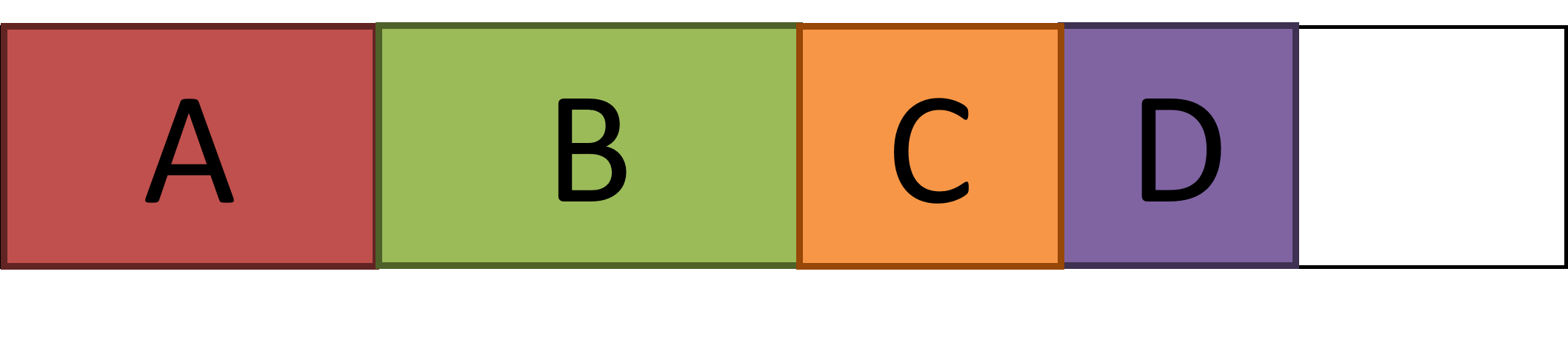
Program C has now closed and is no longer stored in the RAM.
If we did not remove programs that are not active anymore, we would quickly run out of memory. The user wants to open another program called Program E. This could fit in the RAM, however, it cannot fit into one consecutive space. There is enough total free space available – it’s just not located together in a single block.
One possible solution is that we would move Program D into the free space left by Program C so that Program E can be stored in one consecutive space. However, this would take a lot of time and be inefficient. This would reduce the performance of the computer.
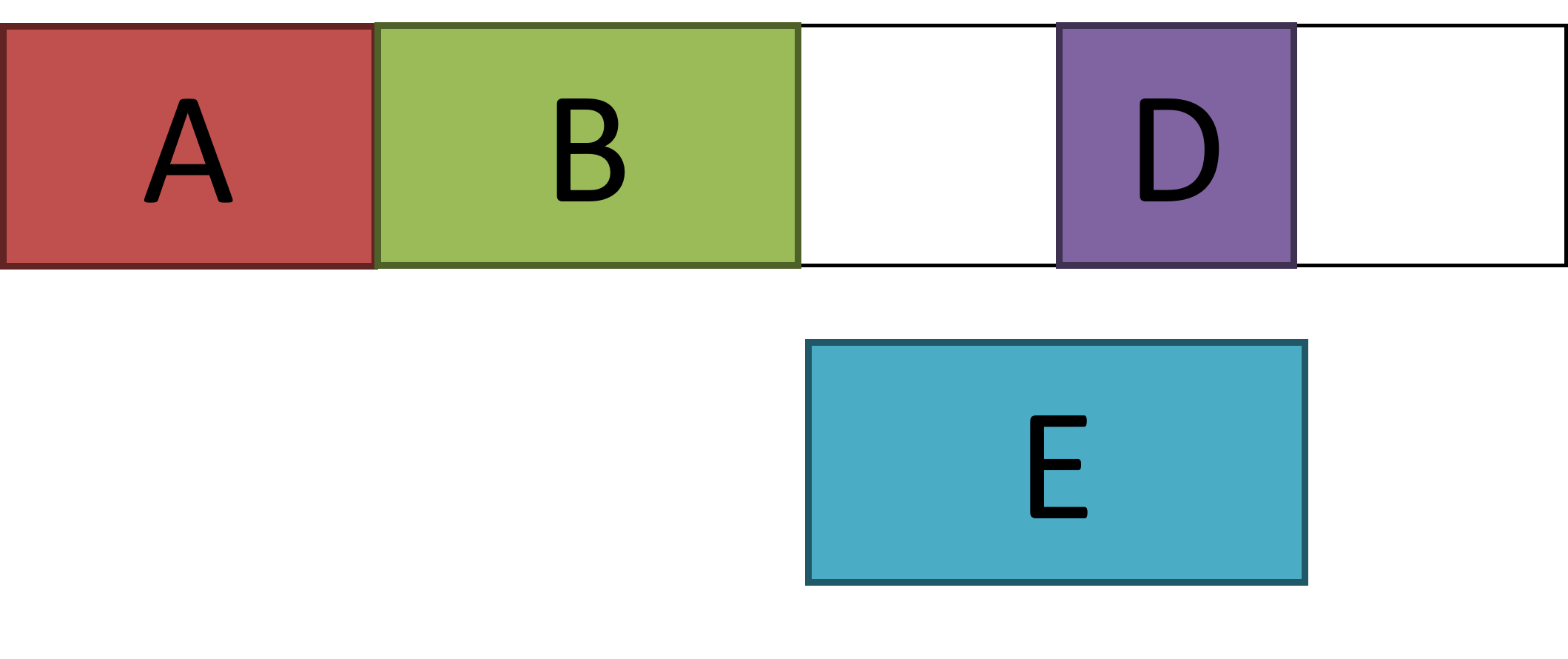
We therefore need a way of managing memory.
What are the two most common ways to manage the memory?
- Paging
- Segmentation
What is paging?
Memory is physically divided into fixed sizes (pages). Active data and programs are split to fit into the pages.
How does paging split active data/programs? What is the problem with the way it splits data / programs?
It does not take into account how it splits the program. The goal of paging is to split active data and programs into fixed size pages regardless of efficiency. The problem is that some data and programs is best kept together in one block. For example, if you have code for a loop that is repeated several times, the code in the loop would be best kept together for efficiency instead of being split across two different areas of memory.
Example of paging
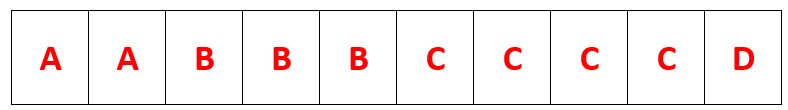
The user has 4 programs called A, B, C and D.

Here is some memory that uses paging. Split up programs A-D and place them into the memory below.
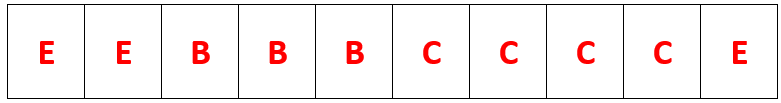
Program A and D have now been closed and removed from memory. Program E has now been added.

What does the memory look like now?
What is segmentation?
Once a program, routine, module or section of a program has started, it can be fetched from one area of memory rather than switching the memory locations. This improves efficiency and therefore the performance of the computer.
Example of segmentation
Here is some memory that makes use of segmentation. The user has 3 programs called A, C and D.
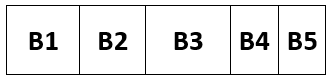
The user wants to load Program B. This consists of 5 subroutines:
Using segmentation, split up program B logically to fit into memory:
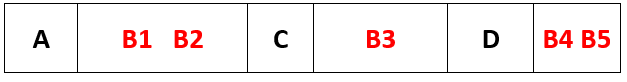
What is the benefit of segmentation?
Once one program, routine, module or section of a program has started, it can be fetched from one area of the memory rather than having to keep switching the memory locations
Virtual Memory is another form of memory management. This was covered in Topic 2.
Craig n Dave video
Interrupts
Interrupts
Topic 3: Operating systems
(3) Interrupts
What is an interrupt?
This is when a device or process signals to the processor that it requires immediate attention of the CPU. If the interrupt is a higher priority than the current task, the CPU will stop the current task and execute the code for the interrupt. Once the interrupt has been processed, the CPU will continue with the program it was dealing with before the interrupt was raised.
Examples of interrupts
- Laptop low on power
- Hardware issues such as a paper jam
- User presses CTRL + ALT + DEL
- Anti-malware has detected a threat
- New hardware device connected
- Timer has run out
- Signal to confirm data transfer is complete
- Arithmetic overflow.
What does the FDE cycle diagram look like with interrupts?
What is the interrupt service routine?
The Interrupt Service Routine (ISR) is a program with its own set of instructions that need to be fetched, decoded and executed to carry out the interrupt.
Look at this example of a CPU that has received an interrupt.
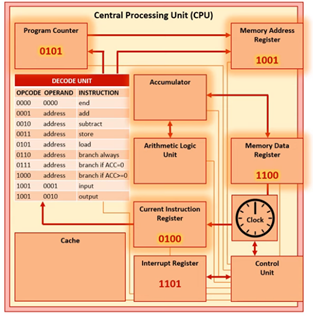
The Program Counter currently stores 0101. An interrupt has been received in the Interrupt Register (IR) and the interrupt is a higher priority than the current task. The first instruction of the Interrupt Service Routine (ISR) is in memory location 1101. Therefore, the value in the Program Counter (0101) is no longer going to be the address of the next instruction to be executed by the CPU.
What would happen if the interrupt address simply replaced the address in the program counter?
Once the interrupt has been dealt with, the CPU will need to return to the instruction it was processing before the interrupt was raised. If we simply replace the PC for the value in the interrupt register, then the CPU will not know where to continue with the suspended program after the interrupt has been completed.
How does the CPU handle an interrupt?
Stage 1 - Before Interrupt
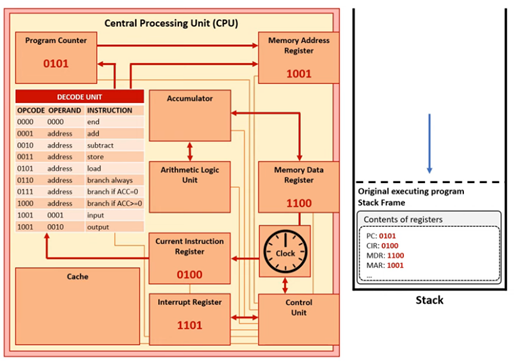
The CPU will complete the current FDE cycle. Interrupts are checked at the end of each FDE cycle. If a new interrupt has been raised, the priority will be checked. If the priority is lower/equal, the current task will continue. If the priority is higher than the current task, the values in the registers will be stored in memory in a data structure called a stack.
Stage 2 - During Interrupt
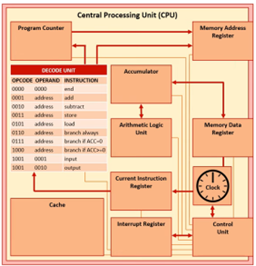
The registers can now be used to handle the interrupt. The Interrupt Service Routine will be loaded. The address of the first instruction of the Interrupt Service Routine is placed into the Program Counter. The CPU will now use the registers to handle the interrupt.
Stage 3 - After Interrupt
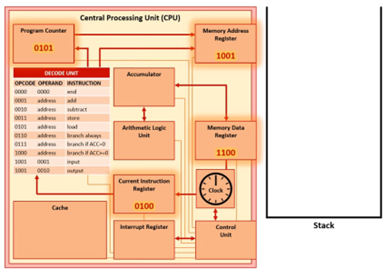
Once the interrupt has been processed, the values stored in the stack are popped and returned to the registers. This allows the CPU to retrieve the instruction it was executing before the interrupt and continue.
What happens if an interrupt is interrupted by another higher priority interrupt?
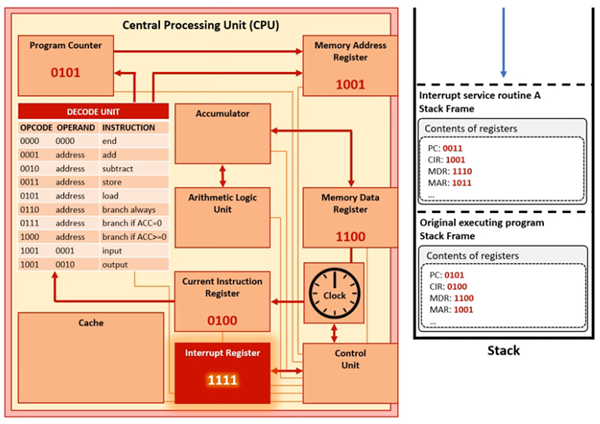
- The CPU will complete the current FDE cycle for the existing interrupt. Interrupts are checked at the end of each FDE cycle.
- The priority of the new interrupt will be checked. If the new interrupt is lower/equal priority to the current interrupt, the current interrupt will continue.
- If the new interrupt is a higher priority than the current interrupt, the contents of the registers will be stored in memory in the same stack.
- The stack now contains the register contents for the original instruction and for the first interrupt.
- The Interrupt Service Routine for the higher priority interrupt will be loaded. The relevant value will be placed into the Program Counter.
- The registers will be used to handle the higher priority interrupt.
- Once it has been handled, the values for the lower priority interrupt will the popped from the stack and returned to the registers to continue.
Craig n Dave video
Scheduling
Scheduling
Topic 3: Operating systems
(4) Scheduling
What is meant by the term 'scheduling'?
This is an algorithm that manages all of the CPU operations that need to be completed at the same time. It manages the order that tasks will be processed and the length of time that they will be executed for.
What is the First Come First Served scheduling algorithm?
All jobs are given equal priority. They are processed in the order they arrive. First in first out (FIFO). Once started, jobs are processed until completion. Jobs have to wait for the current job to finish before they can be processed.
Examples of when FCFS would be used
- Printer queues
- A server handling requests from clients in a network.
What are the benefits and drawbacks of FCFS?
| Benefits | Drawbacks |
|---|---|
| Simple and easy to implement as there are no calculations to determine the queue order. | Once jobs are started then they are processed until completed. Therefore, longer processes can delay smaller processes. |
| A fair way of processing – jobs are executed in the order they arrive. | Jobs cannot be prioritised. |
What is the Round Robin scheduling algorithm?
Each process is allocated a maximum amount of CPU time (a time slice). If a process is not completed in its time slice, it is suspended and joins the queue to wait for another time slice.
What is an example of when Round Robin would be used?
Managing CPU multitasking.
Why does the computer’s operating system uses the round-robin algorithm for allocating processor time?
To allow CPU multi-tasking to take place. This allows the CPU to switch between active processes and those running in the background. Each process is given an equal time slice in quick succession. This gives the impression that the processes are happening at the same time.
What are the benefits and drawbacks of FCFS?
| Benefits | Drawbacks |
|---|---|
| Longer processes will not delay shorter processes. | Jobs cannot be prioritised. |
| A fair way of processing. All jobs get the exact same amount of CPU time. | Spends a lot of time switching between different processes. This involves overheads which lower efficiency and performance of the computer. |
| Simple and easy to implement because there is no need to calculate how much time should be given to each task. They all receive the same maximum amount of CPU time. |
What is the Shortest Job First scheduling algorithm?
This algorithm picks the processes that take the shortest amount of time. The processes are run until completion. This means that longer processes do not delay shorter processes.
What are the benefits and drawbacks of Shortest Job First?
| Benefits | Drawbacks |
|---|---|
| Longer processes will not delay shorter processes. | Longer processes may be starved of CPU time. |
| Reduces average wait time when compared to FCFS. | You have to sort the jobs into execution order. This involves overheads which lower efficiency/performance of the computer. |
| Faster than Shortest Time Remaining because the CPU does less switching. |
What is the Shortest Remaining Time scheduling algorithm?
This algorithm will choose the process that has the shortest amount of time to execute. However, the job will be suspended if another job with a shorter processing time comes in.
What are the benefits and drawbacks of Shortest Time Remaining?
| Benefits | Drawbacks |
|---|---|
| Longer processes will not delay shorter processes. | Longer processes may be starved of CPU time if lots of smaller jobs keep coming in. |
| Reduces average wait time when compared to FCFS. | You have to sort the jobs into execution time order. This involves overheads which reduce the efficiency/ performance of the computer. |
What is the Multi-Level Feedback Queues scheduling algorithm?
When one computer system has several processors/processing cores, it can handle more than one queue at a time. Different queues can be given different priorities. Jobs can be moved between queues.
What are the benefits and drawbacks of Multi-Level Feedback Queues?
| Benefits | Drawbacks |
|---|---|
| This is the most flexible as it allows different processes to move between different queues. | Switching between queues can produce more CPU overheads. |
| Prevents starvation by moving a process that waits too long for the lower priority queue to the higher priority queue. | It is the most complex algorithm. The others are simpler. |
Craig n Dave video
OS Types
OS Types
Topic 3: Operating systems
(5) OS Types
| Operating System | Explanation | Example use |
|---|---|---|
| Multi-Tasking | This allows multiple programs to run at the same time. The CPU will allocate each process an equal time slice in quick succession. This gives the impression that multiple processes are happening at the same time. This allows the CPU to manage active processes and those running in the background. |
All of these tasks can run at the same time:
|
| Multi User | This allows multiple users to use a computer at the same time. The OS will manage user permissions, user access rights and user preferences. They are commonly used on servers to be able to handle requests from multiple people at the same time. An operating system that has multiple different accounts but only allows one of them to be logged on at the same time is NOT a multi-user operating system. It is a single-user operating system. |
|
| Distributed | They combine the processing power of multiple computers to work together on a single task. The OS controls and coordinates the computers. |
|
| Embedded | Embedded systems have a dedicated and limited function. They are built into another device. They are used to control a specific piece of hardware. It is stored in ROM and cannot be changed. They tend to have low powered processors and little storage. |
|
| Real-Time | They will respond to changes or user inputs in a guaranteed time frame. They have plenty of redundancy to be able to handle sudden increases in user inputs. |
|
Why are real-time operating systems suitable for intensive care units?
If something happens to patient, the response must be immediate. Real time will respond in a guaranteed time frame. Other types of system may have a delay. This could result in the patient not receiving the treatment.
What is meant by overlapping classifications?
Operating system classifications overlap. This means that an OS may be more than one type. Look at these examples:
| Benefits | Drawbacks |
|---|---|
| A server managing requests from multiple clients on a network. |
|
| Car safety system that responds to dangers on the road. |
|
| A multiplayer online game. |
|
Craig n Dave video
BIOS
BIOS
Topic 3: Operating systems
(6) BIOS
What does BIOS stand for?
Basic Input Output System
Where is the BIOS stored?
This is stored on the ROM chip inside the computer.
What is the BIOS used for?
It is used to start up the computer and for device settings. Without BIOS, your computer would not know what to load up when you first turn on the computer.
What does the BIOS do when you first turn on your computer?
- BIOS is loaded from ROM into RAM.
- BIOS checks what hardware is available.
- BIOS checks that the hardware is working correctly via POST checks (Power-On-Self-Test). This includes CPU, Memory, GPU and Motherboard.
- It finds the operating system, loads it into main memory and passes control over to it.
What settings can you change in BIOS?
You can select which drive your computer will boot from – e.g. if your hard drive has corrupted, you might want to boot from a recovery drive instead. Sometimes, you can increase/change the clock speed in BIOS. This is known as overclocking.
Craig n Dave video
Device Drivers
Device Drivers
Topic 3: Operating systems
(7) Device Drivers
What is a peripheral device?
This is a device outside of the computer such as a monitor, keyboard, mouse etc.
What is a device driver?
This is a small piece of software that tells the operating system how to communicate with a peripheral device. It will translate operating system instructions into a series of instructions that the specific piece of hardware can understand.
Why is a device driver needed?
Peripheral devices are all made by different manufacturers and to different standards. Device drivers allow the operating system to communicate with the peripheral device.
Peripheral devices that may need a device driver
- Printer
- Scanner
- Digital camera
- Webcam
What happens when you connect a new piece of hardware into the computer?
The operating system will attempt to find a suitable device driver for the new piece of hardware. The OS will come with thousands of drivers built-in. However, if it cannot find a driver, it will ask you to provide this. This is usually on an installation CD that comes with the hardware or it can be downloaded from the internet.
Craig n Dave video
Virtual Machines
Virtual Machines
Topic 3: Operating systems
(8) Virtual Machines
What is a virtual machine?
This is when a program runs on one computer but it behaves like another computer. It can be configured to replicate the hardware and software of another device. It is often a window that runs a different operating system or program.
Uses of virtual machines
- Running alternative operating systems: They allow the installation of one operating system within another operating system. This could include a legacy OS. This means you don’t need another physical computer.
- Supporting incompatible software: Some older software might not run on newer systems. A VM could emulate an older system, on which the user could run the old software.
- Creating a test environment: VMs are a closed and controlled environment. This provides the opportunity to run software that could be damaging, such as malware, without damaging the computer.
- Running multiple servers: Servers on networks are required to fulfil multiple roles, such as providing access to file storage or storing email accounts for users. More than one server can run on a VM, which allows for the separation of services without the need for multiple physical pieces of hardware.
What is a problem with compiling code into machine code?
With traditional programming, code is compiled into machine code that is specific to one device. This therefore makes it difficult to run the compiled code on lots of different devices.
How can this issue be solved using intermediate code?
Intermediate code is produced by the compiler. Rather than compiling the code fully into machine code, the code can be compiled half-way. Therefore, the code is partially compiled but not completely. This is known as intermediate code. The code can be compiled further on different devices into the specific machine code for that device. This therefore allows code to run on different devices. This makes the code more portable between machines because it can run on any computer. It also protects the source code from being copied.
Craig n Dave video
Topic 4: Application Software
Application Software
Application Software
Topic 4: Application generation
(1) Application software
What is application software?
This is software that allows the user to solve problems or complete tasks for example:
- Create word-processed documents
- Create spreadsheets
- Create databases
- Create graphics
Application software
| Software | Description | Tools | Basic tasks |
|---|---|---|---|
| Word processing software | Allows you to create, edit, store and print documents. Word processors are generally used for the production of business or personal documents that contain a lot of text. |
|
|
| Desktop publishing software | Allow users to combine images and text to create publications. DTP is used to create and position graphical objects onto the page (including text) using frames. |
|
|
| Spreadsheet software | Enables the user to produce models, and to produce graphs to graphically represent data. They are used to process numerical data however can handle some text. |
|
|
| Database software | Database packages enable users to store and organise data. Once stored it allows the user to handle the data such as sorting and searching. |
|
|
| Graphics software | Graphics software allows you to create and edit graphics. This can then be used and then inserted into other documents. |
|
|
| Web authoring software | Allows you to create websites. This has built-in tools to enable well-designed web pages to be created with a variety of features to meet the needs of the users. |
|
|
| Presentation software | Allows you to create electronic presentations. It contains slides that contain content that will be shown during a presentation. |
|
|
Craig n Dave video
Utilities
Utilities
Topic 4: Application generation
(2) Utilities
What is utility software?
A piece of software with one purpose. They are designed to manage, monitor and maintain the computer system. The aim is to keep the computer running safely and efficiently.
Does the user install the utilities or are they included with the Operating System?
The operating system will include a wide range of utilities. However, the user can install additional specialised utilities.
How does an application differ from a utility?
Applications perform tasks for the user rather than the computer.
Common utilities
- File repair
- Backup
- Data compression
- Defragmentation
- Security
- Device drivers
- System cleanup
What is a file repair utility?
Files can become corrupt or damaged. File repair utilities attempt to correct these issues and restore the files to their original working state.
What is a backup utility?
A backup utility will keep a copy of data on another secondary storage device (e.g. cloud, external hard drive). This therefore means that if something was to happen to the original data, you can use the backup (copied data) to restore the data.
When would you need to restore data from a backup?
If something happens to the original data. For example:
- Fire
- Theft
- Virus
What are two types of backup?
- Full
- Incremental
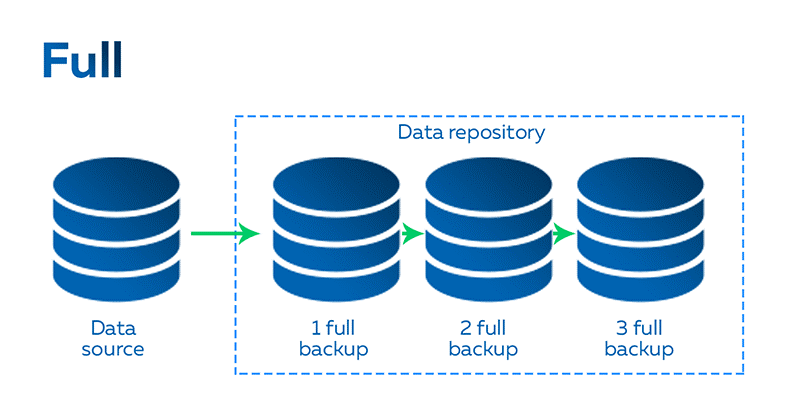
What is meant by the term 'full backup'?
- All files and folders on the drive are backed up every time a backup occurs.
- You are able to restore data fast because you can simply do this from the last full backup.
- However it takes a long time to backup your data as all data had to be copied.
- It requires a lot of additional storage space every time you want to backup. It also stores lots of duplicated data.
Diagram of a full backup
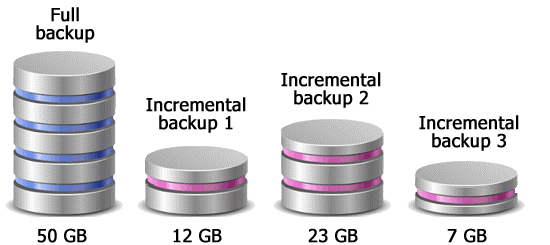
What is meant by the term 'incremental backup'?
- Makes an initial full backup to begin with.
- Then only new or updated data is backed up each time a backup is made.
- It requires several backups to restore data.
- It can be slow to restore because you have to restore data from several increments.
- However it can be quick to backup your data as only new and updated data needs to be copied.
- It requires a less storage space because you are not saving duplicated data.
Diagram of an incremental backup
What does a data compression utility do?
Compression utilities will use algorithms to reduce the amount of storage space that a file takes up. Often the algorithms will look for data that is repeating and remove repeated data from a file.
Two types of compression
- Lossy - PERMANANTLY removes some data from the file. Significantly reduces the file sizes.
- Lossless - Makes the file smaller but DOES NOT PERMANANTLY remove data from the file.
What are the benefits of compression?
- Reduces the file size. This therefore reduces space on disk / servers. This is also useful as most people have limited data allowances on their mobile data.
- Reduce the amount of time it takes to download and upload data.
- Reduce the amount of bandwidth needed.
- Reduces buffering as the data packets being sent / loaded are smaller.
Example of compression
In the paragraph below, there are a nuymber of items of data which are repeated:
The size of an image file depends on the colour depth and dimensions. The size of an audio file depends on the sample rate and bit depth. The size of an image file and audio file can be very large.
| Number | Word | No. of times in text |
|---|---|---|
| 1 | The | 5 |
| 2 | Size | 3 |
| 3 | Of | 3 |
| 4 | An | 3 |
| 5 | Image | 2 |
| 6 | File | 4 |
| 7 | Depends | 2 |
| 8 | On | 2 |
| 9 | And | 3 |
| 10 | Depth | 2 |
| 11 | Audio | 2 |
Once each word has been stored, it does not need to be stored several times. Therefore, it will be stored once and then every time it appears a copy of the original word will appear.
What is meant by the term 'fragmented file' and why is it caused?
- Over time, you will save files on your hard drive.
- You will then delete files which will free up space on your hard drive.
- However when you save new files, it may not fit into a space from a previously deleted file.
- Therefore it may not fit on the disk in consecutive storage locations so the file becomes fragmented (scattered), otherwise known as separated and stored in different locations across the hard drive.
What does the disk defragmentation do?
Disk defragmentation will put fragmented/separated files and free space back together again and store them in consecutive storage locations.
Diagrams of before and after defragmentation:
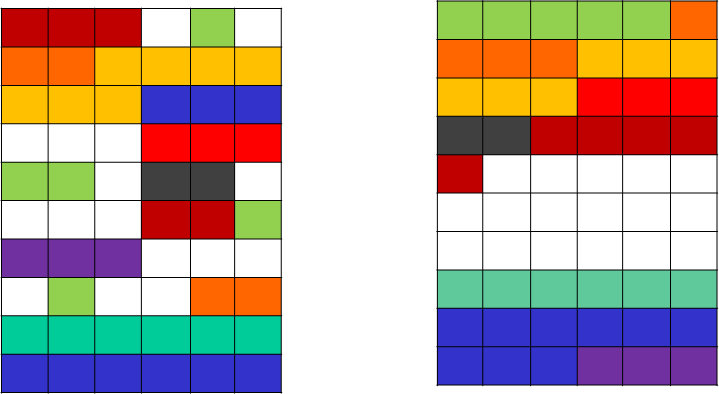
Why does disk defragmentation improve the performance of the computer?
The hard drive will be able to find files faster. This is because the read/write head will not need to move across the platter(disk) as many times when:
- finding files
- writing new files to the hard drive
What is the purpose of security utilities?
The purpose of utility software is to ensure that the computer system is protected against any threats such as hacking, viruses, Trojans, worms and spyware. It will remove or quarantine infected files to stop them doing any damage to the computer.
What security utilities does your operating system likely include?
- Anti-Malware – Prevent malware / viruses
- Firewall – Prevents hacking / unauthorised access
What is the purpose of clean up utilities?
Clean-up utilities will remove files that are no longer needed or files that can be safely deleted. The aim is to free up storage space on the hard drive.
What files are covered by clean up utilities?
- Compression of old files
- Temporary internet files
- Temporary windows files
- Downloaded program files
- Recycle bin
- Removal of unused applications or optional windows components
What is a device driver?
This is a small piece of software that tells the operating system how to communicate with a peripheral device. It will translate operating system instructions into a series of instructions that the specific piece of hardware can understand.
Craig n Dave video
Open v Closed
Open v Closed
Topic 4: Application generation
(3) Open v Closed
What is meant by 'open source' software
This is software that is made freely available online. Users can legally modify the source code to create their own ‘version’ of the software.
What is expected by the Open Source Initiative when using 'open source' software
- Software is licensed for use but there is no charge for the license. Anyone can use it
- Open Source software must be distributed with the source code so anyone can modify it
- Any new software created from Open Source software must also be ‘open’. This means that it must be distributed or sold in a form that other people can read and also edit.
Benefits and drawbacks of open source software to USERS
| Benefits | Drawbacks |
|---|---|
| It is (usually) free – but not always. This means money can be saved. | There may be limited documentation. |
| The user can inspect/amend/recompile the source code to meet their individual needs. | Some features might not be well tested. |
| Usually have a strong community. Any problems are quickly solved by a community of people. | As lots of people can modify the code there could be hundreds of different versions of the same program which may make it harder to get help. |
| Code is open for bugs to be spotted and fixed. |
Benefits and drawbacks of open source software to CREATORS
| Benefits | Drawbacks |
|---|---|
| You are able to quickly share your software with the community. | If you are using open source software to create new software, you have to freely share your code (including with competitors). |
| More people are likely to use your software if they don’t have to pay for it. | You get little-to-no financial gain for the software that you have produced. |
What is meant by closed source software?
This is software where the source code is kept a closely-guarded secret. Software providers don’t allow you to view the computer code or allow you to modify the programming code. It is protected by the copyright, design and patents act.
Examples of closed source software
- Adobe Photoshop
- Microsoft Windows
- Microsoft Office
- Adobe Fireworks
How does licensing work with closed source software?
- The company/person who wrote the code will hold the copyright
- The user does not own the software, only a licence to use it.
- The licence may specify only one user, or it may permit up to say, 50 users on one site (site licence)
- The users will not have access to the source code and will not be allowed to modify the package and sell it to other people.
Advantages and disadvantages of closed source software to USERS
| Advantages | Disadvantages |
|---|---|
| Comes with lots of documentation and good customer support. | Can be very expensive to buy. |
| They are well tested and very reliable. Companies will often release updates to fix any errors or bugs. | Software may not meet your exact needs and you cannot modify the programming code. |
| Software companies may not maintain older software when they expire. For example Microsoft no longer support Windows XP. |
Advantages and disadvantages of closed source software to CREATORS
| Advantages | Disadvantages |
|---|---|
| They can receive income from their software. | They may have to keep updating the software to take into account new threats. |
| The programming code cannot be copied by another company. | Users may copy the software and therefore they may not get paid for their work. |
Comparison of features
| Feature | Open Source | Closed Source |
|---|---|---|
| Cost | It is (usually) free – but not always. | Can be very expensive to buy. |
| Documentation | There may be limited documentation. There could be hundreds of different versions of the same program available. | Comes with lots of documentation and good customer support. |
| Adaptation To Needs | Software can be adapted to meet the individuals needs. | Software may not meet your exact needs and you cannot modify the programming code. |
| Amount of Testing / Reliability | May have limited testing and therefore as its free there it may not always be reliable. | They are well tested and very reliable. Companies will open release updates to fix any errors or bugs as people are paying for the software. |
Craig n Dave Video
Translators
Translators
Topic 4: Application generation
(4) Translators
Differences between high-level and low-level languages
| Low level languages | High level languages |
|---|---|
| It is written for ONE type of CPU. | It is written for MANY types of CPUs. |
| This is language the CPU can understand. | This is language the CPU DOES NOT understand. |
| It doesn’t need translating so its more efficient when its executed. | It DOES need translating so its less efficient when its executed. |
What is the purpose of a translator?
To convert high level language into low level machine code.
Two different translators that can be used
- Compiler
- Interpreter
Interpreters explained
- It translates each line of code ONE AT A TIME and executes it immediately before moving onto the next line of code.
- An interpreter is needed every time you want to run the program.
- Programs will run more slowly because the code is being translated as the program is running.
- It will run until it reaches its first error and it will then stop.
- No object code is produced.
Advantages and disadvantages of Interpreters
| Advantages | Disadvantages |
|---|---|
| The program will still run until it reaches its first error before stopping. | Runs slowly as each line is interpreted one at a time. |
| It’s easier to debug as individual lines of code can be tested. | The interpreter is needed each time the program is run. |
Diagram of how an Interpreter works
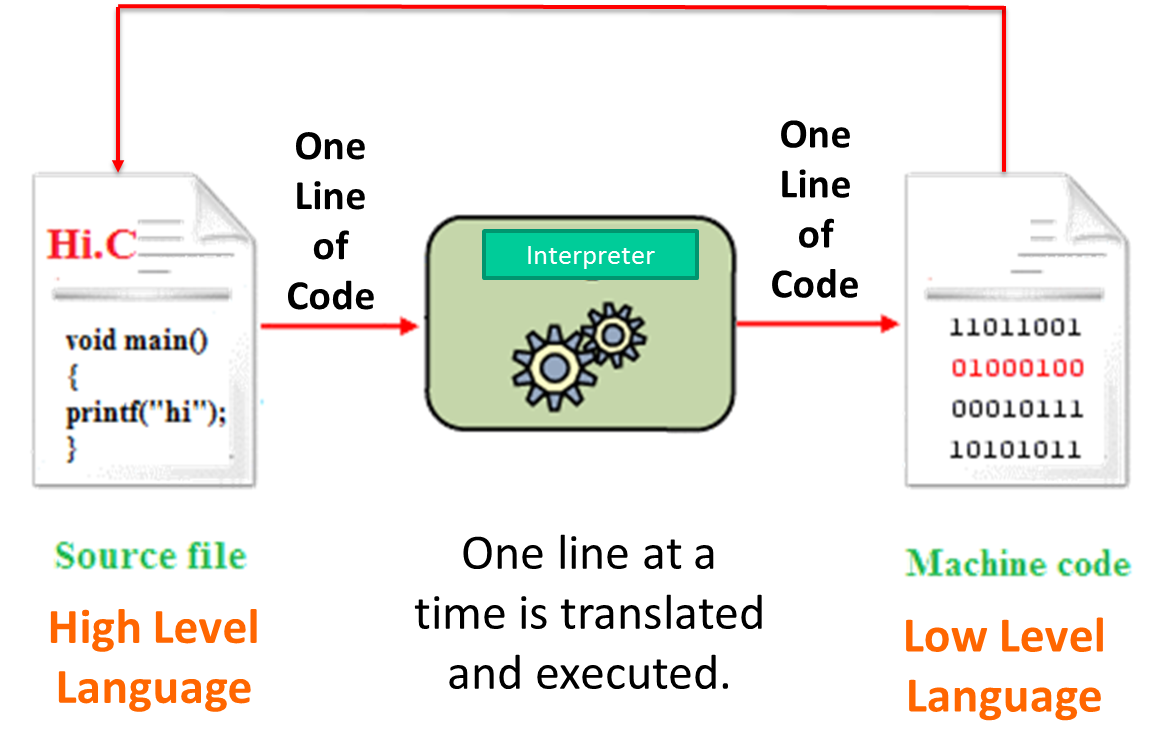
Compilers explained
- It translates ALL of the source code at the same time and creates one executable file.
- Its only needed ONCE to create the executable file.
- Once its compiled the program runs quickly as its already all in machine language.
- However its difficult to test an individual line of the code and so will return a list of errors for the entire program.
- The code written by the programmer is called the source code. The code produced by the compiler is called the object code.
Advantages and disadvantages of Compilers
| Advantages | Disadvantages |
|---|---|
| Runs very fast (once its compiled) | Difficult to debug code as it’s hard to test individual lines of code. |
| The compiler is only needed once to create the executable file. | The code will not run at all if there is an error. |
Diagram of how a Compiler works
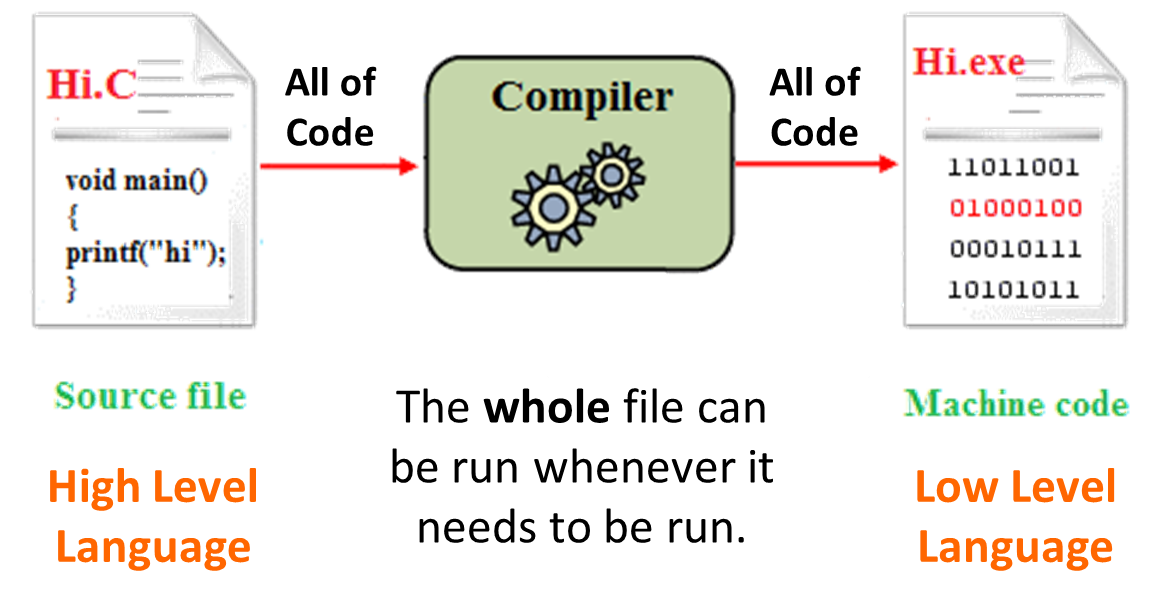
What is an assembly language and why is it needed?
Assembly languages allow programmers to write code at low level. Low level languages would require programmers to write code using 1s and 0s which would be difficult. Assembly language makes this easier by allowing them to use mnemonics. These are short commands that can be converted directly into 1’s and 0’s.
What is needed to translate assembly language into machine code?
An assembler
Craig n Dave Video
Code Compilation
Code Compilation
Topic 4: Application generation
(5) Code Compilation
What is meant by the term 'code compilation'?
Programmers write source code which is a high level programming language (such as Python). However, this needs to be turned into machine code. In order to do this, the compiler has to run through a series of stages. Each stage will perform different actions on the source code.
Stages of code compilation
| Stage | Description |
|---|---|
| Phase 1 - Lexical Analysis |
For example:
|
| Phase 2 - Syntax Analysis |
|
| Phase 3 - Code Generation |
|
| Phase 4 - Code Optimisation |
|
Craig n Dave Video
Libraries etc
Libraries, Linkers & Loaders
Topic 4: Application generation
(6) Libraries, Linkers & Loaders
What is a software library?
These are sections of code that have already been written by other authors. They contain useful routines for common tasks so that the user does not need to write themselves.
Examples of software libraries that exist in programming languages
- GUI routines
- Database access routines
- Encryption
- Graphics
Benefits and drawbacks of using libraries
| Benefits | Drawbacks |
|---|---|
| Save time and money because less code needs to be written. | May increase size of compiled file as often libraries contains many routines that aren‘t used. |
| Less specialist knowledge needed. You can use the expertise of others to complete tasks that require specialist knowledge. | Although you can use the libraries, you often don’t know how they actually work. This internal workings are hidden (you are "black boxed"). Therefore, you don’t know how efficient the code is. |
| The code will have already been pre-tested so the programmer doesn’t have to test it themselves. | You may not be able to change the code. Therefore, changing it to meet your needs is difficult |
What is a linker?
After the code has been compiled, the linker will then connect the object code to the library. If static linking is used, the object code and libraries will be combined into a single executable file. If dynamic linking is used, the executable code will point to the library when in use. The library will then be loaded into main memory when the executable file is running.
Diagram of a linker
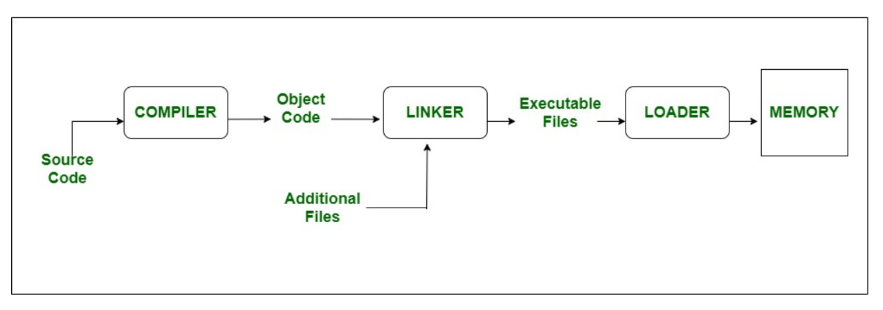
What is meant by the term 'static linking'?
This is when all of the required code from the libraries are included in the finished executable file. This results in large executable file sizes.
What is meant by the term 'dynamic linking'?
This is when the library is not part of the final executable file. Instead, the linker will point the executable code to where the library is saved on the host computer when in use. The library will be stored in main memory whilst the code is running. This cuts down on the file size of the final executable program, however, if the library can’t be found on the host computer, the program won’t work.
What is a loader?
The loader is the part of the operating system that actually loads the executable program file into memory so that it is ready to run.
What will the loader do if you have used dynamic linking?
It will load the required libraries into memory so they are ready when called.
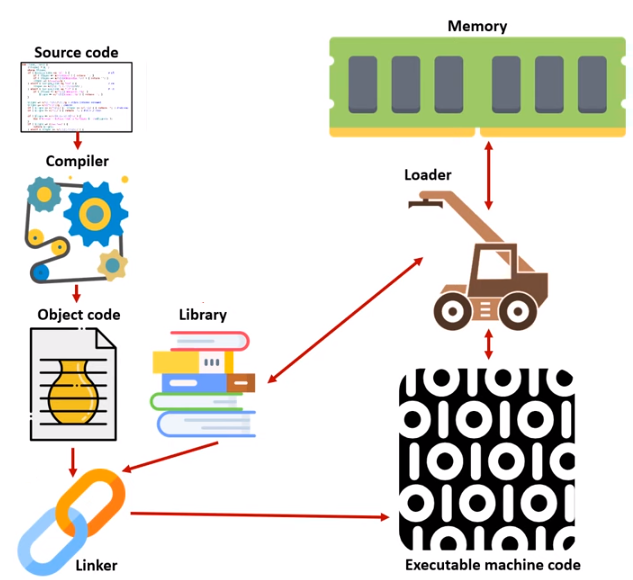
Craig n Dave Video
Topic 5: Software Methodologies
Methodologies
Software Methodologies
Topic 5: Software Methodologies
(1) Methodologies
What is a software methodology?
This is how time in a project is spent and the order in which tasks are completed.
List software methodologies in the specification
- Waterfall lifecycle
- Agile methodologies - a group of iterative methodologies sharing common principles.
- Spiral model
- Rapid Application Development
What are the factors that should be considered when choosing a software methodology?
- Is the project big or small? (Note: A big project does not mean that its complex)
- Is the project simple or complex? (Note: A big project does not mean that its complex)
- Are the project requirements clearly defined?
- Are the project requirements likely to change?
- How much involvement does the client have in the project?
- How quickly is the software needed?
- How much risk is involved in the project?
- Does the project need to be delivered in stages or in one go?
Waterfall Lifecycle
Although this methodology is considered somewhat outdated, it is still used because of its simplicity and clear structure. It has several stages (analysis, design, development, test and evaluate) and these are completed in order. At the end of each stage a decision will be made to move onto the next stage.
When would this be used?
- For small or large projects (as it’s easy to manage).
- Suitable for simple projects.
- When the requirements are clearly defined.
- When the requirements are not likely to change during the project.
- When the client does not need a lot of involvement in the project.
- When the software is not needed quickly.
- When there is little risk in the project.
- If the project can be delivered at the very end.
| Benefits | Drawbacks |
|---|---|
| Can be used on big projects or small projects. | Not suitable for complex projects. |
| Less client involvement means there is less burden on the project team. | Not suitable if the requirements may need to change during the project. |
| It has clear structured stages – e.g. analysis, design etc. so everyone in the team knows their responsibility. | Limited client involvement so little opportunity for feedback. Prototypes not created until late in the project. This causes a risk that the client will be unsatisfied at the end of the project. |
| Team members are responsible for one area (e.g. analysis) so they know their responsibilities. | Projects generally have increased development time. |
Agile Methodologies (Iterative methodologies)
Note: This is not a single methodology. Instead it refers to a group of iterative methodologies that all use the same principles. Iterative means the project is split and done in stages. Each of the methodologies that are based on the agile approach have slight variations to them. For example, the Extreme Programming methodology is based on Agile. The focus is on producing high quality code.
Using these methodologies, the project is completed in smaller phases (iterations) known as sprints. Each sprint is given a time box of 1-4 weeks maximum. Each phase (sprint) has a focused goal which is planned, developed, tested and reviewed before the next phase starts. The end-user also gets to see prototypes much earlier and provide feedback that can feed into the next stage.
When would this be used?
- For small or large projects
- Suitable for simple or complex projects
- When the requirements are NOT clearly defined
- When the requirements ARE likely to change during the project
- When the client DOES need a lot of involvement in the project
| Benefits | Drawbacks |
|---|---|
| It’s easy to change the requirements once the project has started. | It requires the project team to work in close collaboration with each other. |
| The client has lots of involvement so therefore they are able to give lots of feedback to reduce problems at the end. | Lots of client involvement can be a burden and slow down development time. |
| You develop prototypes early and can deliver the project in stages. | |
| Projects (usually) have a reduced development time. |
What is meant by the term extreme programming?
This is a software methodology that is based on an agile approach (e.g. an iterative approach). The main difference is that the programming code is the main priority. Its focus is to produce high quality programming code instead of producing high quality documentation. It often uses pair programming where two (or more programmers) will create the programming code together.
Rapid Application Development
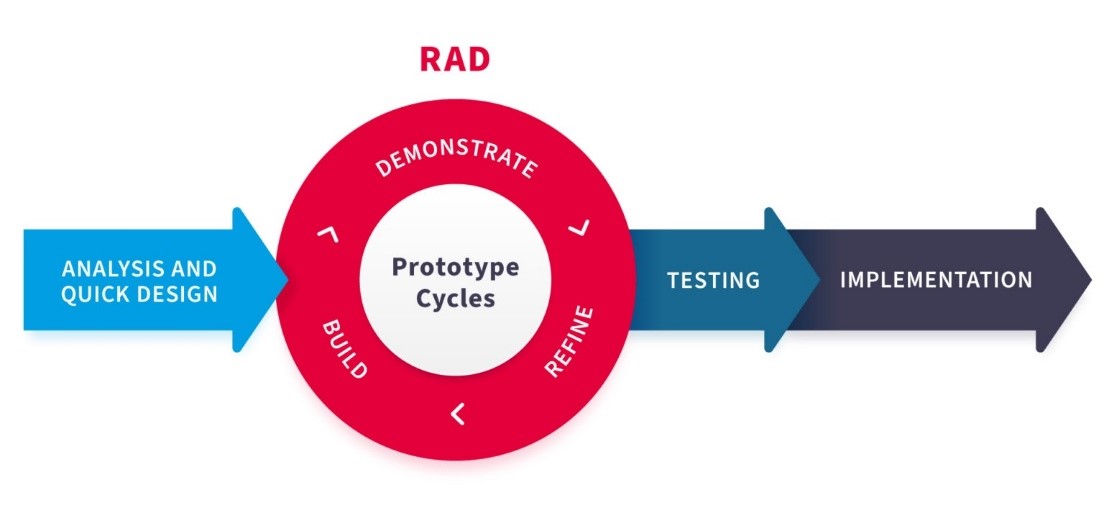
A quick feasibility study is conducted and, once approved, a prototype is designed, coded, tested and evaluated by the end user. Based on this, the prototype is then either refined or the next prototype is developed.
- For smaller projects
- For simple projects
- When the requirements are NOT clearly defined
- When the requirements ARE likely to change during the project
- When the client DOES need a lot of involvement in the project
- When the software IS needed quickly
| Benefits | Drawbacks |
|---|---|
| It’s easy to change the requirements once the project has started. | The focus is on the quality of the usability and not creating quality code. |
| The client has lots of involvement so therefore they are able to give lots of feedback to reduce problems at the end. | Lots of client involvement can be a burden and slow down development time. |
| You develop prototypes early and can deliver the project in stages. This allows early user feedback and faster iteration. | Often the software is ‘good enough’ to meet immediate needs rather than being fully polished. |
| Projects (usually) have a reduced development time. | Not suitable for large teams/projects or for complex projects. |
Spiral Model
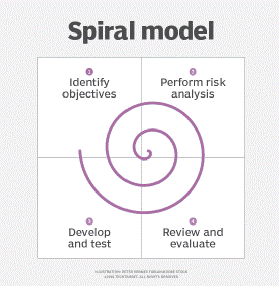
This is a risk driven methodology and focuses on prototyping. It allows teams to adopt elements of one or more other software methodologies. It consists of four key areas:
- Identify objectives
- Perform risk analysis
- Analysis
- Develop/Test
- Review/Evaluate
The stages are not followed in order because the order will be determined by the amount of risk in the project. Spiral relies on lots of client feedback. The stages may be repeated or revisited in a non-linear order dependent on project risks.
When would this be used?
- When there is a LOT of risk involved in the project
- For large and complex projects
- When the requirements are NOT clearly defined
- When the requirements ARE likely to change during the project
- When the client DOES need a lot of involvement in the project
| Benefits | Drawbacks |
|---|---|
| Ideal for projects that contain high risk or unknown factors. | The number of phases is unknown at the start of the project. |
| It’s easy to change the requirements once the project has started. | Not suitable for small or simple projects. Better for large teams/projects with complexity. |
| The client has lots of involvement so therefore they are able to give lots of feedback to reduce problems at the end. | The end of the project is not always known. |
| You develop prototypes early and can deliver the project in stages. | The risk analysis needs to be done properly or this can lead to inaccurate decisions being made. |
| Projects (usually) have a reduced development time. |
Craig n Dave videos
Assembly Language
Assembly Language
Topic 5: Software Methodologies
(2) Assembly Language
What is a programming paradigm?
A paradigm is a style or “way” of programming that can be used to solve a problem. One language may use one paradigm while others may use more than one.
Three programming paradigms
- Procedural
- Object-Oriented
- Assembly
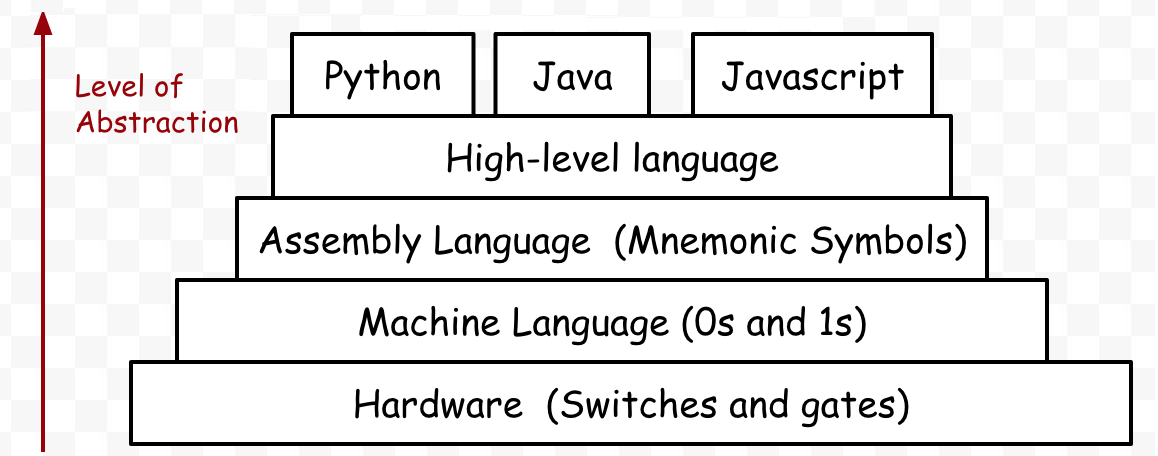
What is assembly language and why is it needed?
Assembly languages allow programmers to write code at low level. Low level languages would require programmers to write code using 1s and 0s which would be difficult. Assembly language makes this easier by allowing them to use mnemonics. These are short commands that can be converted directly into 1’s and 0’s.
Why would a programmer want to program in assembly language?
- To access device specific functionality.
- It allows you to make the best use of hardware such as the CPU or memory.
- When code is translated from a high level language to a low level language, this may not be the most efficient way possible. Writing at a low level means that you can fine-tune the instructions before translating to machine code.
Some translators will convert high level code into assembly language first to allow you to fine-tune the instructions before converting it into machine code.
Is assembly language transferrable between different CPUs?
Each CPU has its own unique instruction set. This means that you can write assembly instructions that are specific to that individual CPU. This means that assembly instructions (and machine code) written for one CPU will not work on another CPU.
What is needed to translate assembly language into machine code?
An assembler - NOTE: You do not need to know how an assembler works.
How is assembly code different to high level languages?
| High level languages | Assembly languages |
|---|---|
| The code is written in English words. | The code is written using mnemonics. |
| Translated using a compiler or interpreter. | Translated using an assembler. |
| Works across multiple different CPUs. | Works on one specific CPU. |
Why might software intended for one device not work on another device?
- The author may have used Digital Rights Management (DRM) to protect software from being able to run on anything other than the intended system.
- Different devices may have different processors each with their own instruction sets.
- Different devices may have different operating systems but the software might be dependent on a libraries that don't exist on the other operating system or make different calls.
- Software might only be available on a certain type of media (e.g. DVD or Blu-Ray). This may not be supported by another device.
Craig n Dave video
Little Man Computer
Little Man Computer
Topic 5: Software Methodologies
(3) Little Man Computer
What is Little Man Computer?
The LMC is used to simulate how assembly language works. It has only 11 commands written in mnemonics which can be used to build programs. In reality, a CPU would have hundreds of assembly commands.
LMC's 11 Commands
| Command | What does this do? |
|---|---|
| ADD | Add a number at a stated address to whatever is in the accumulator. |
| SUB | Subtract a number at a stated address from whatever is in the accumulator. |
| STA | Store the contents of the accumulator in a stated memory address. |
| LDA | Copies the contents from a memory address to the accumulator. |
| BRA (Branch always) | Branch to the stated address/label without checking the accumulator. |
| BRZ (Branch if zero) | Branch to the stated address/label if zero is in the accumulator. |
| BRP (Branch if zero or positive) | Branch to the stated address/label if zero or a positive number is in the accumulator. |
| INP | Take an input and put it into the accumulator. |
| OUT | Output the value in the accumulator. |
| HLT | End the program. |
| DAT | Used for data. |
Code written in LMC will often look like this:
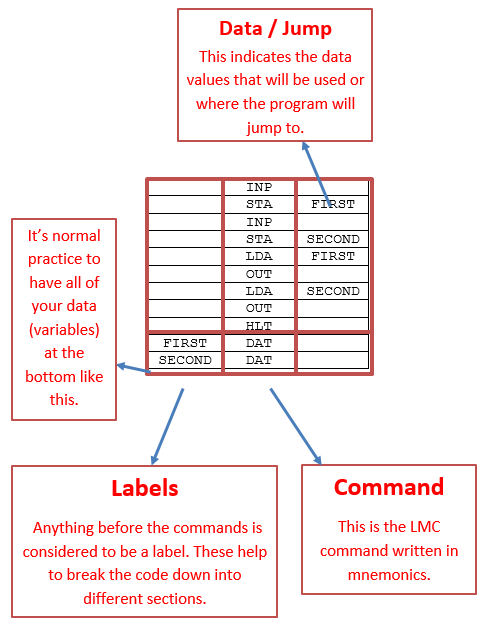
Example Program 1
A program using the LMC instruction set that will:
- Input a number and then output it.
| INP | ||
| OUT | ||
| HLT |
Example Program 2
A program using LMC instruction set that will:
- Input two numbers
- Output both numbers separately (first followed by the second)
| INP | ||
| STA | FIRST | |
| INP | ||
| STA | SECOND | |
| LDA | FIRST | |
| OUT | ||
| LDA | SECOND | |
| OUT | ||
| HLT | ||
| FIRST | DAT | |
| SECOND | DAT |
Example Program 3
A program using LMC instruction set that will:
- Input two numbers
- Add them together
- Output the result
| INP | ||
| STA | Num1 | |
| INP | ||
| ADD | Num1 | |
| OUT | ||
| HLT | ||
| Num1 | DAT |
Example Program 4
A program using LMC instruction set that will:
- Input two numbers
- Add them together
- Output the total
- Allow a third number to be entered
- Subtract the total away from the third number
- Output the overall total
| INP | ||
| STA | FIRST | |
| INP | ||
| ADD | FIRST | |
| OUT | ||
| STA | TOTAL | |
| INP | ||
| SUB | TOTAL | |
| OUT | ||
| HLT | ||
| FIRST | DAT | |
| TOTAL | DAT |
Example Program 5
A program using LMC instruction set that will:
- Input two numbers
- Output the largest of the two numbers
NOTE: If the values are equal, both numbers represent the largest value, so either can be output.
| INP | ||
| STA | FIRST | |
| INP | ||
| STA | SECOND | |
| SUB | FIRST | |
| BRP | SECONDBIG | |
| LDA | FIRST | |
| OUT | ||
| BRA | PROGRAMEND | |
| SECONDBIG | LDA | SECOND |
| OUT | ||
| PROGRAMEND | HLT | |
| FIRST | DAT | |
| SECOND | DAT |
Example Program 6
A program using LMC instruction set that will:
- Repeatedly ask for a number to be input until 3 is entered.
- When 3 is entered, the program should stop.
| loop | INP | |
| SUB | num | |
| BRZ | end | |
| BRA | loop | |
| end | HLT | |
| num | DAT | 3 |
Example Program 7
A program using LMC instruction set that will:
- Output the values from 1 to 10
This should use a loop.
| LDA | ONE | |
| STA | COUNT | |
| OUT | ||
| LOOPTOP | LDA | COUNT |
| ADD | ONE | |
| OUT | ||
| STA | COUNT | |
| SUB | TEN | |
| BRP | ENDLOOP | |
| BRA | LOOPTOP | |
| ENDLOOP | HLT | |
| ONE | DAT | 001 |
| TEN | DAT | 010 |
| COUNT | DAT |
Example Program 8
A program using LMC instruction set that will:
- Input a number
- Square the number (multiply the number by itself)
| INP | ||
| STA | num | |
| loop | LDA | total |
| ADD | num | |
| STA | total | |
| LDA | count | |
| ADD | one | |
| STA | count | |
| SUB | num | |
| BRZ | end | |
| BRA | loop | |
| end | LDA | total |
| OUT | ||
| HLT | ||
| one | DAT | 1 |
| num | DAT | 0 |
| count | DAT | 0 |
| total | DAT | 0 |
Example Program 9
A program using LMC instruction set that will:
- Input a number
- Count downwards from this number and output this..
- ..until the first negative number is reached
| INP | ||
| STA | COUNT | |
| OUT | ||
| LOOPTOP | LDA | COUNT |
| SUB | ONE | |
| STA | COUNT | |
| OUT | ||
| BRP | LOOPTOP | |
| HLT | ||
| COUNT | DAT | |
| ONE | DAT | 1 |
Example Program 10
A program using LMC instruction set that will:
- Input a number
- The program will count upwards from this number and output each one...
- ..until 20 is reached
| INP | ||
| STA | COUNT | |
| OUT | ||
| LOOPTOP | LDA | COUNT |
| ADD | ONE | |
| OUT | ||
| STA | COUNT | |
| SUB | TWENTY | |
| BRP | ENDLOOP | |
| BRA | LOOPTOP | |
| ENDLOOP | HLT | |
| ONE | DAT | 001 |
| TWENTY | DAT | 020 |
| COUNT | DAT |
Example Program 11
A program using LMC instruction set that will:
- Input a number
- The program will then round the number upwards to the nearest multiple of ten
- Output the result
| INP | ||
| main | STA | entry |
| BRA | test | |
| fail | LDA | entry |
| ADD | one | |
| BRA | main | |
| test | SUB | ten |
| BRZ | pass | |
| BRP | test | |
| BRA | fail | |
| pass | LDA | entry |
| OUT | ||
| HLT | ||
| entry | DAT | |
| ten | DAT | 10 |
| one | DAT | 1 |
Example Program 12
A program using LMC instruction set that will:
- Input a number
- The program will then ask the user to enter the amount of numbers specified
- Output the addition of all the numbers
For example, if the user entered 3, it will then ask the user to enter three numbers, add them together and then output the total
| INP | ||
| STA | NoOfNos | |
| LOOP | INP | |
| STA | NUM | |
| ADD | TOTAL | |
| STA | TOTAL | |
| LDA | NoOfNos | |
| SUB | ONE | |
| STA | NoOfNos | |
| BRZ | PROGEND | |
| BRA | LOOP | |
| PROGEND | LDA | TOTAL |
| OUT | ||
| HLT | ||
| NUM | DAT | |
| NoOfNos | DAT | |
| ONE | DAT | 1 |
| TOTAL | DAT |
Example Program 13
A program using LMC instruction set that will:
- Input two numbers, num1 and num2
- Output the results of multiplying these two numbers: num1 x num2
HINT: you will have noticed that there are two instructions for adding (ADD) and subtracting (SUB) numbers. There is no instruction for multiplying two numbers. The solution to overcome this is to consider a multiplication as a series of additions. For instance: 5 * 4 = 5 + 5 + 5 + 5
| INP | ||
| STA | NUM1 | |
| INP | ||
| STA | NUM2 | |
| LOOP | LDA | NUM2 |
| BRZ | END | |
| LDA | TOTAL | |
| ADD | NUM1 | |
| STA | TOTAL | |
| LDA | NUM2 | |
| SUB | ONE | |
| STA | NUM2 | |
| BRA | LOOP | |
| END | LDA | TOTAL |
| END | OUT | |
| HLT | ||
| NUM1 | DAT | |
| NUM2 | DAT | |
| ONE | DAT | 1 |
| TOTAL | DAT | 0 |
Tracing LMC Code
Example 1
| INP | ||
| main | STA | entry |
| BRA | test | |
| fail | LDA | entry |
| ADD | one | |
| BRA | main | |
| test | SUB | ten |
| BRZ | pass | |
| BRP | test | |
| BRA | fail | |
| pass | LDA | entry |
| OUT | ||
| HLT | ||
| entry | DAT | |
| ten | DAT | 10 |
| one | DAT | 1 |
What would the output be if the input was 18?
Answer: 20
The best way to work this out is using a table. It should have the accumulator and then all of the variables. For example, the above would have the accumulator, entry, one and ten. You should also have an out box.
| Accumulator | 18 8 -2 18 19 9 -1 19 20 10 0 20 |
| Entry | 18 19 20 10 |
| Ten | 10 |
| One | 1 |
| Out | 20 |
What would the output be if the input was 37?
Answer: 40
What is the purpose of this program?
To round upwards to the nearest 10
Example 2
Here is some LMC code:
| INP | ||
| STA | num | |
| loop | LDA | total |
| ADD | num | |
| STA | total | |
| LDA | count | |
| ADD | one | |
| STA | count | |
| SUB | num | |
| BRZ | end | |
| BRA | loop | |
| end | LDA | total |
| OUT | ||
| HLT | ||
| one | DAT | 1 |
| num | DAT | 0 |
| count | DAT | 0 |
| total | DAT | 0 |
State the output for 1
Answer: 1
State the output for 2
Answer: 4
State the output for 3
Answer: 9
What is the purpose of this program
To square a number / multiply a number by itself
Example 3
| start | INP | |
| STA | donation | |
| SUB | hundred | |
| BRP | bonus | |
| nobonus | LDA | total |
| ADD | donation | |
| STA | total | |
| OUT | ||
| BRA | start | |
| bonus | LDA | total |
| ADD | donation | |
| ADD | twenty | |
| STA | total | |
| OUT | ||
| BRA | start | |
| hundred | DAT | 100 |
| twenty | DAT | 20 |
| donation | DAT | 0 |
| total | DAT | 0 |
The program shown is run once using three different inputs. Give the values that are output when the values 10, 50 and 120 are input into this program.
State the output for 10
Answer: 10
State the output for 50
Answer: 60 (50 added to previous)
State the output for 120
Answer: 200 (140 added to previous)
Craig n Dave Videos
Addressing Modes
Addressing Modes
Topic 5: Software Methodologies
(4) Addressing Modes
As we know, active data/instructions are stored in the RAM. The CPU has to fetch these from the RAM so that they can be processed. In order to fetch instructions from RAM, the locations have to be addressed so we know where to find them.
What are the different modes of addressing
- Immediate
- Direct
- Indirect
- Indexed
Once an instruction has been fetched, it then has to be decoded and then executed. During the decode stage, it will split the binary code into an opcode and operand.
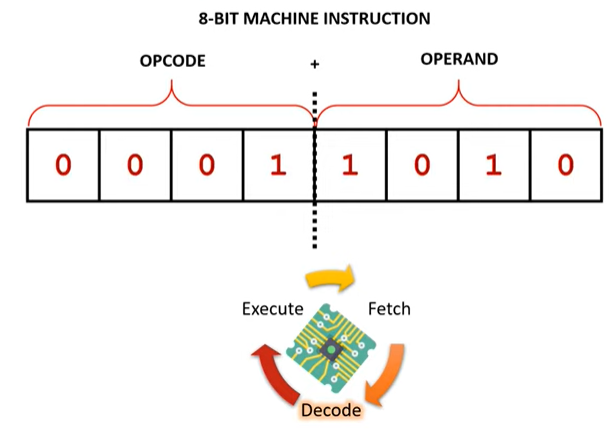
What is the difference between Opcode and Operand?
- Opcode: Specifies the type of instruction to be executed. The instruction type above is 0001.
- Operand: Contains the data or the address of the data. The data above is 1010..
Once the opcode has been established, what will it then do?
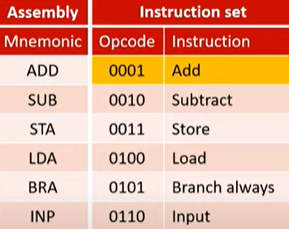
It will look it up in the instruction set. In this case, the opcode 0001 means ADD.
Now we know the opcode is ADD, what do we need to establish next?
We need to establish what data we are adding. The value in the Operand 1010 could mean lots of different things dependent on what mode of addressing has been used.
Immediate Addressing
In this example, immediate addressing is used. We know the operand is 1010. It therefore has the denary value 10. We also know that the opcode means ADD.

What will it therefore do?
It will add 10 to whatever is currently in the accumulator. It does NOT mean add the value in memory location 10.
What is immediate addressing?
This means that the operand holds the actual value to be used.
Benefit and drawback of immediate addressing
| Benefits | Drawbacks |
|---|---|
| Allows simple access to data with no fetch required. | The denary value of the data stored in the operand is limited to 0-15. This is because the operand is only 4 bits. |
Direct Addressing
In this example, direct addressing is used. We know the operand is 1010. It therefore has the denary value 10. We also know that the opcode means ADD.
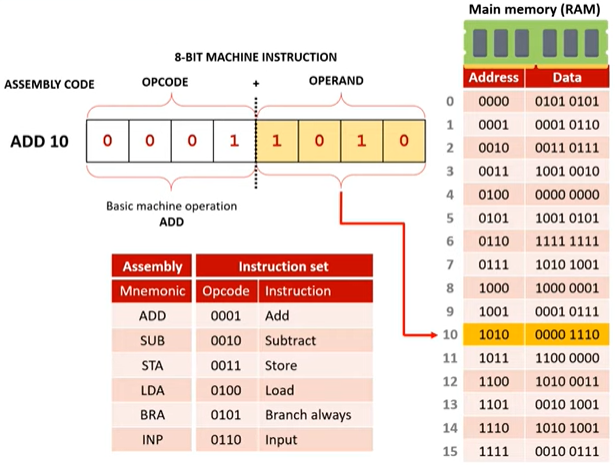
What will it therefore do?
It will NOT add the value 10. Instead, it will add the value that is in memory location 10. The value in location 10 is 0000 1110. It will therefore add 14 to the accumulator
What is direct addressing?
This means that the Operand holds the address of the data to be used.
Benefit and drawback of Direct Addressing
| Benefits | Drawbacks |
|---|---|
| Allows data to be fetched from memory. | The address range is limited to 0-15 because the size of the operand is 4 bits. |
| The data can be larger in size (0-255) than with immediate addressing because there are 8 bits available instead of 4. |
Indirect Addressing
In this example, indirect addressing is used. We know that the operand is 1010. It therefore has a denary value of 10. We also know that the opcode means ADD.
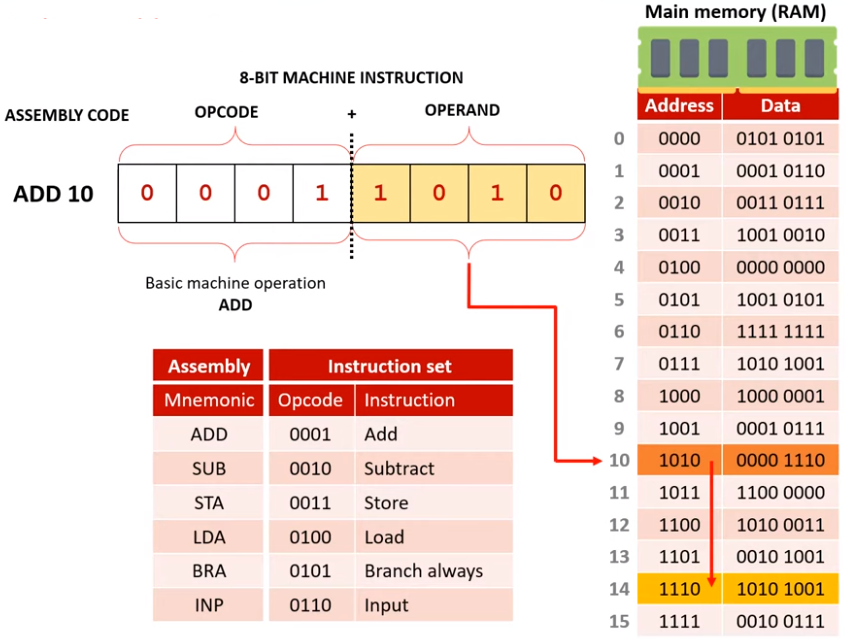
What will the instruction do?
It will NOT add the value 10. Instead, it will add the value that is in memory location 10. Here, it will find another address (0000 1110, which is 14 in denary). It will then go to that address and whatever is there (1010 1001, which is 169 in denary) will be added to the accumulator.
What is indirect addressing?
This means that the Operand contains a memory location which refers to another memory location where the data can be found.
Why is indirect addressing used?
It means that large address ranges can be used (0-255) to reference data and instructions.
Problem with direct addressing
The following example uses direct addressing. How many unique addresses can be achieved? Why?
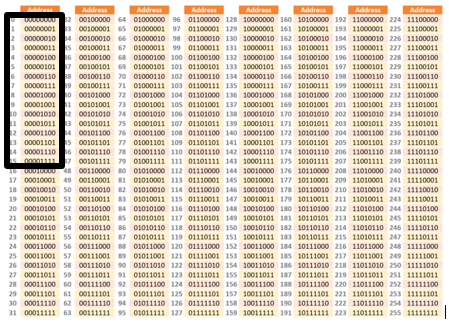
Answer – 16 unique addresses between 0-15. Although there are 256 combinations of 1s and 0s (0-255). We can only have the first 16 unique addresses because there are only 4 bits available in the operand for direct addressing. With 4 bits we can only reference the first 16 memory locations. If direct addressing is used, it would be pointless adding more memory beyond the first 4 bits.
How can indirect addressing solve this problem?
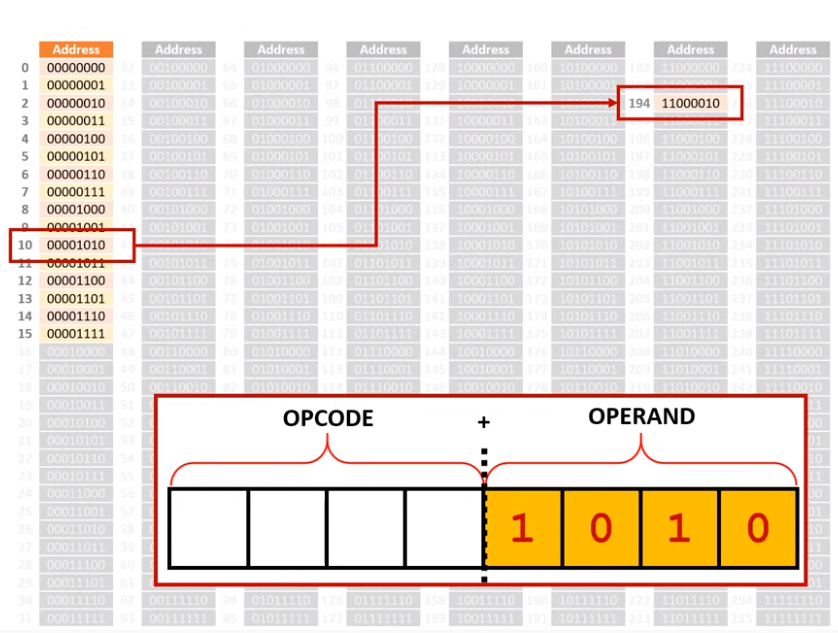
It allows us to reference more addresses. Using indirect addressing, we can now have access to the full 256 memory addresses between 0-255.
Benefit and drawback of Indirect Addressing
| Benefit | Drawback |
|---|---|
| Allows a larger range of addresses to be fetched from. | Multiple fetches required to access data. |
Indexed Addressing
In this example, indexed addressing is used. It will add 3 items together starting at position 10. Therefore, we need an instruction for ADD10, ADD11, ADD12 and ADD13. We would therefore need the same instruction repeatedly. A more efficient way of doing this is to use an index register..
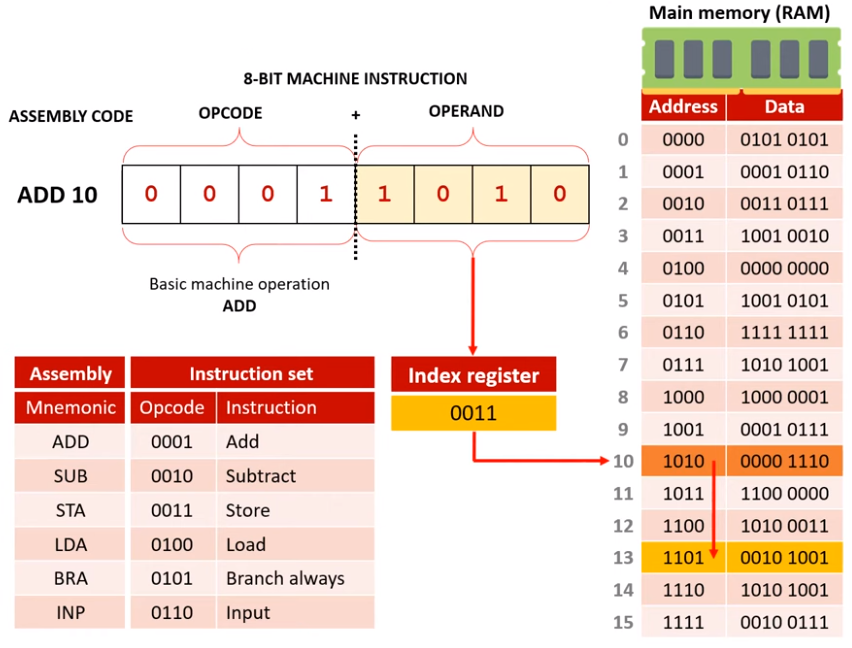
How does Indexed Addressing work?
Indexed Addressing adds the value in Index Register to the value in the Operand to find what memory location to use.
How is the Index Register used?
Initially, the index register is set to 0. This is added to the contents of the operand, which is 1010 (10). The first memory location is therefore 10 (10+0). Once this is done, the index register is incremented by 1 and the same instruction is used again. This time the memory location to use is 11 (10+1). This is why an address needs to be stored in contiguous memory locations. We store the address for element 0 of an array in the index register and then increment.
What will indexed addressing do in this example?
In this case, it will go to memory location 10, plus the value in the index register (3). It will therefore repeat the ADD instruction on memory locations 10, 11, 12 and 13. The final value will be stored in the accumulator.
What is indexed addressing?
This is when the operand is added to the contents of the index register to get the memory location needed. Indexed addressing is where the operand holds the address which is offset using the index register to find the true address of the data to be used.
Benefit of indexed addressing
Benefit - Indexed addressing allows the Index register to be manipulated to access data stored sequentially e.g. in an array.
Recap of Addressing Modes
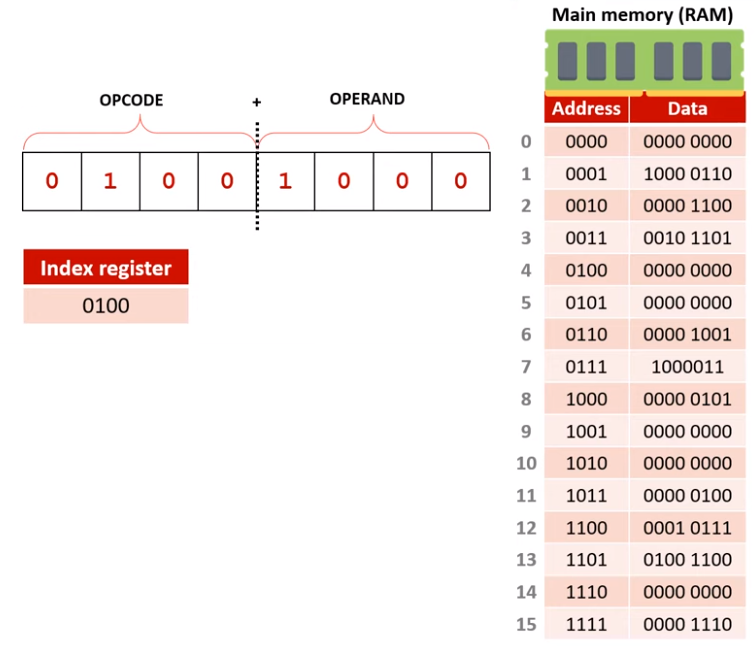
The assembly code is LDA 8 (Load 8). What value will be held in the accumulator if the following address modes are used?
| Addressing Mode | Value in Accumulator | Denary Value |
| Immediate | 1000 | 8 |
| Direct | 0000 0101 | 5 |
| Indirect | 0000 0000 | 0 |
| Indexed | 0001 0111 | 23 |
Craig n Dave video
Topic 6: Databases
Database Basics
Database Basics
Topic 6: Databases
(1) Database Basics
What is a database?
A database is an organised collection of structured data. The data is stored in Tables (entities).
What are the benefits of an electronic database?
- It is easier to retrieve, add, delete and modify data.
- It is easier to backup and make copies of data.
- The database can be accessed by multiple people at the same time from different locations.
Key database terminology
| Term | Definition | Example |
|---|---|---|
| Entity, Table | An entity contains records of data about something. | A table called Songs that contains records about Songs. |
| Record, Row, Tuple | A record is a single row within a table. | In a table about Students, each record would contain fields about an individual student. |
| Attribute, Column, Field | A field is a single item of data within a record. | In a table about Students, each record might contain fields such as firstname, surname, DOB, telephone, etc. |
What is a primary key?
| Primary Key (PK) | |
| Definition | A primary key is a field (or several fields) that give each record a unique identity. The primary key must be unique. It cannot be repeated otherwise it will not be unique. |
| Example |
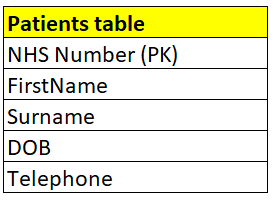
In this example, the primary key NHS number is used to give each record a unique identity. |
In a table for songs, why would Title be unsuitable as a primary key?
A primary key must uniquely identify each record. Title would be unsuitable because two songs could have the same name. This means the title could repeat across records so the primary key would not be unique.
What is a foreign key?
| Foreign Key (FK) | |
| Definition | A foreign key field links to a primary key field in another table. Foreign keys are used to create links (relationships) between tables in a relational database. The foreign key is used to refer to records associated with a primary key in another table. |
| Example |

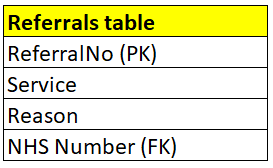
We have used the primary key from the Patients table (NHS Number) in the Referrals table. This allows the Referrals table to link its records to a patient. |
What is a composite key?
| Composite Key | |
| Definition | A composite key is when the primary key has two or more fields. In combination, those fields give each record a unique identity. |
| Example |
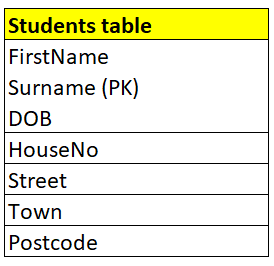
In this example, there is a composite primary key made up of FirstName, Surname and DOB. Together, these fields give each record a unique identity. |
What is a secondary key?
| Secondary Key | |
| Definition | Secondary keys allow another field to be indexed other than the primary key. We can then quickly search or sort the database using the secondary key as the criteria. This is useful if the primary key would be difficult to remember when querying data. |
| Example |

In this example, we have indexed Surname as a secondary key. This means that we can quickly search or sort the database by surname. Surname is much easier to remember than a person’s NHS number. |
What is referential integrity?
| Referential Integrity | |
| Definition | Referential integrity ensures that changes are consistent across a database. Firstly, if the primary key for a record is removed, all references to that primary key are removed from the database. Secondly, a foreign key value must have a corresponding primary key value in another table. |
| Example |
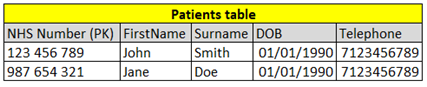
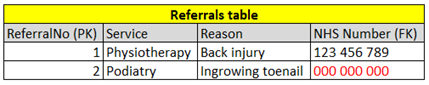
In this example, a value of 000 000 000 has been entered under the foreign key NHS Number in the Referrals table. The problem is, that value doesn’t exist under the primary key. Referential integrity would not allow this. |
What is a relationship?
| Relationship | |
| Definition | A relationship is a link between tables in a relational database. This occurs when a foreign key is used to refer to records associated with a primary key in another table. |
| Example |


In the above example, a relationship was created when the primary key from the Patients table (NHS Number) was used in the Referrals table as a foreign key. |
What is meant by indexing primary keys?
A database is only useful if we can query (retrieve) information quickly. Databases are able to query data quickly by indexing primary keys. Just like an array, the index provides the position of a record according to its primary key. This makes the retrieval of records referenced by the index much quicker. The alternative to indexing primary keys is searching records sequentially (one at a time, in order).
What would be a benefit and drawback of indexing Artist in a Songs table?
| Benefits | Drawbacks |
|---|---|
| Searches of Artist can be performed more quickly. | The index takes up extra space in the database. |
Why would DestinationCode be a suitable secondary key for a table containing details of Flights?
It is likely to be used to search for/index/sort records in the Flights table.
What is a flat file?
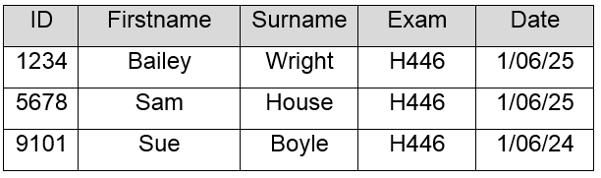
A flat file database has only one table. Flat files are quick and simple to setup. They require little expertise. They are suitable for storing small amounts of data, such as contact information. Flat files use comma-separated values (CSV).
What are the benefits and drawbacks of a flat file?
| Benefits | Drawbacks |
|---|---|
| Flat files can be quick and simple to setup. | They are slow to query (retrieve) data from. |
| They are suitable for storing small amounts of data. | Not suitable for storing large datasets. |
| They require little expertise to maintain. | Flat file databases become less efficient as they grow in size. |
What is a relational database?
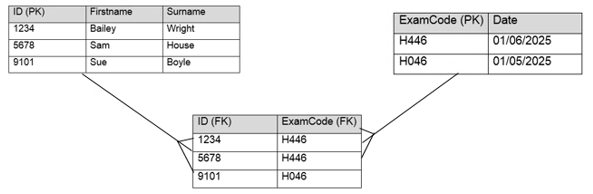
A relational database contains multiple tables that are linked together using primary and foreign keys. The links are called relationships.
What are the benefits and drawbacks of a relational database?
| Benefits | Drawbacks |
|---|---|
| Less redundant, repeated and inconsistent data. | Relational databases are complex. This means that expertise is necessary to setup and maintain them. |
| Easier to expand in the future. | |
| Accessing/querying data may be faster. |
Craig n Dave Videos
Normalisation
Normalisation
Topic 6: Databases
(2) Normalisation
What is Normalisation?
Normalisation is the concept of splitting tables in a database and arranging data so that it complies with the rules of First, Second and Third Normal Form.
What are the benefits of normalisation?
- The database will take up less storage space.
- The database will be simpler/easier to maintain because it is more efficient.
Un-Normalised Form (0NF) characteristics:
0NF means the database is a flat file, with only one table, that does not comply with 1NF.
First Normal Form (1NF)
- Every table must have a primary key.
- No two records should be identical.
- Field names must be unique.
- Fields should contain only one single value (i.e. it must be atomic).
- Fields should contain only one type of data (e.g., dividing Name into FirstName and Surname fields).
Second Normal Form (2NF)
- The database is already compliant with 1NF.
- Any partial dependencies have been removed.
What is a partial dependency?
| Definition | A partial dependency is when a field is only dependent on part of a composite primary key. |
| Example |
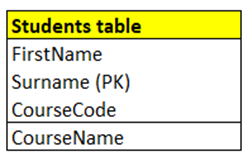
In this example, there is a composite primary key made up of FirstName, Surname and CourseCode. There is, however, a partial dependency because the CourseName field is only dependent on part of the primary key. Namely, the CourseCode. |
How can you avoid a partial dependency in a database?
You can ensure that a table only serves one purpose. For example, a table with student data should only store student data, not information about courses.
What are the characteristics for Third Normal Form (3NF)?
- The database is already normalised to 2NF.
- Any transitive dependencies (also known as non-key dependencies) have been removed.
What is a transitive (non-key) dependency?
| Transitive (non-key) dependencies | |
| Definition | A transitive (non-key) dependency is when a field is dependent on a field that is not part of the primary key. |
| Example |
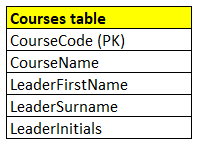
In this example, there is a transitive (non-key) dependency because the LeaderInitials field is entirely dependent on the LeaderFirstName and LeaderSurname fields. All fields must be dependent on the key, the whole key and nothing but the key. |
Craig n Dave Videos
Downloads
Entity Relationship Diagrams
Entity Relationship Diagrams
Topic 6: Databases
(3) Entity relationship diagrams (ERDs)
What is an Entity Relationship Diagram (ERD) and why are they used?
This is a diagram that shows the relationships between tables in a relational database. Examples include:
- One-to-One
- One-to-Many
- Many-to-Many
Symbols used for each type of relationship
| Relationship | Symbol |
|---|---|
| One-To-One |

|
| One-To-Many |

|
| Many-To-Many |

|
These two tables have a many to many relationship. What is the problem?
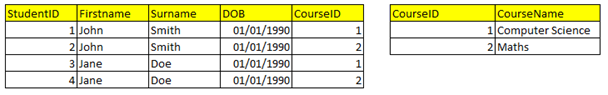
To assign John Smith and Jane Doe to two courses each, we had to duplicate the firstname, surname and DOB fields. We also had to assign two student numbers to John and Jane. This is unnecessary repeating data.
This is an alternative solution. What is the problem this time?
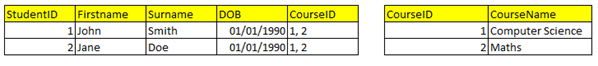
This time, to assign John and Jane to two courses each, we had to put two values into the CourseID field. This breaks the rules of 1st Normal Form which does not allow more than one value to be entered into a field.
A database stores information about songs on a music streaming service. One of the tables called Songs has the fields Title, Artist, Genre and Length. There are multiple Playlists that are stored in a Playlists table. Why is a third table which we shall call PlaylistEntry is needed?
The PlaylistEntry table is needed because there is a many-to-many relationship.
- Many songs can be added to many playlists.
- Many playlists can have many songs.
To resolve this, the PlaylistEntry table should be added:

- One song can have many playlist entries.
- A playlist entry can only have one song.
- A playlist entry can only have one playlist.
- One playlist can have many playlist entries.
Downloads
SQL
SQL
Topic 6: Databases
(4) SQL
An excellent resource for learning SQL can be found HERE. Please complete this.
What is SQL and what is it used for?
SQL means Structured Query Language and it is used to query and manipulate data within a relational database.
SQL Commands
You must learn the following commands:
| Command | Meaning | Example |
|---|---|---|
| SELECT | Retrieve records from a table. |
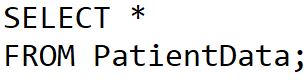
|
| WHERE | Allows you to only execute a command on certain records WHERE certain criteria is met. |
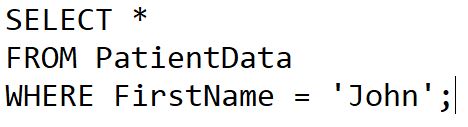
|
| AND | This allows you to apply more than one WHERE criteria. |
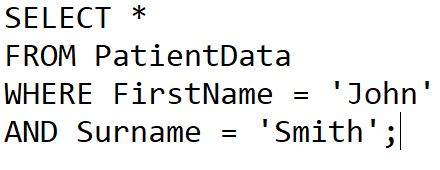
|
| OR | This allows you to retrieve records WHERE x OR y criteria is met. |
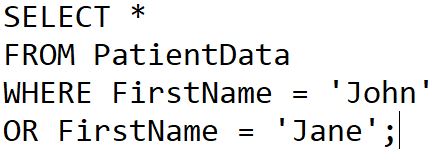
|
| LIKE | This is used to search for a pattern when a where search is being carried out. |
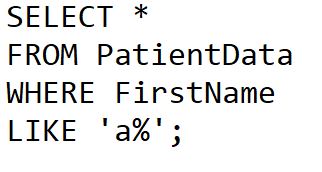
|
| INSERT | Insert records into a table. |
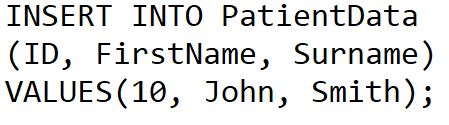
|
| UPDATE | Update an existing record in a table. |
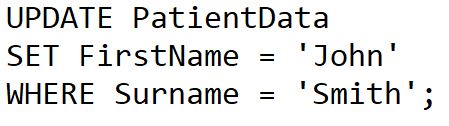
|
| DELETE | Delete a record from a table where a condition is met. |
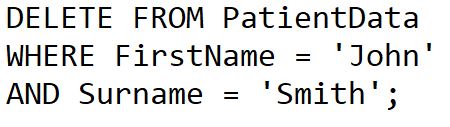
|
| JOIN (same as INNER JOIN) | Allows you to query from multiple tables at the same time in a relational database using primary and foreign keys. |

|
| DROP | Deletes a whole table and its records permanently. |
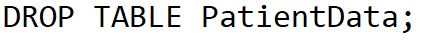
|
| SORT BY - ASCENDING |

|
|
| SORT BY - DESCENDING |

|
Craig n Dave Video
Downloads
Data Management
Data Management
Topic 6: Databases
(5) Data Management
Phase 1: Data Capture
Before data can be entered into a database, it must be captured. This can be captured using manual or automatic data capture methods.
| Method | Major Benefit | Major Drawback |
|---|---|---|
| Paper forms | Handwriting can be used as a method of data collection. | Poor legibility could make it difficult for the person to understand what has been written on the form. |
| Electronic forms | Data capture is not affected by poor handwriting. | May be difficult to update and edit once created. Some users may find this difficult to use. |
What are the different automatic ways to capture data?
| Method | Major Benefit | Major Drawback |
|---|---|---|
| Sensors | Allows measurements to be recorded accurately at all times of day. This is effective for reading license plates in the dark. | May record data incorrectly which will require human intervention |
| Optical Character Recognition (OCR) | This helps to speed up and automate data input. The technology automatically reads text by interpreting the shape of letters. This works far better with printed text than handwriting. | Less effective with handwriting if legibility is poor. |
| Optical Mark Recognition (OMR) | Fast and efficient way of collecting data and inputting into a database whilst significantly reducing the possibility of human error. Often used for multiple-choice tests and lottery tickets. | If the marks don’t fill the space completely, or aren’t in a dark enough colour, they may not be read. |
Phase 2: Data Selection
Once data has been collected and entered into a database, you need to be able to select data that you want to use.
What is meant by SQL?
SQL (Structured Query Language) is a common query language used to retrieve information from a database. SQL allows fast and efficient retrieval, deletion and manipulation of data using a simple set of commands such as SELECT, FROM and WHERE.
What is meant by QBE?
QBE (Query by Example) is a graphical query language. QBE makes use of visual tables where the user would enter commands and conditions. Many of the graphical front-ends of databases such as Microsoft Access implement ideas from QBE. Once a query is built using QBE, it is converted into statements that can be executed against the database.
Similarities and Differences between SQL and QBE
With QBE, the user doesn’t need to remember how to write SQL syntax. They only need to understand how to use the graphical user interface.
Both SQL and QBE allow you to specify tables, fields, criteria, output sorting, and to use Boolean expressions (AND, OR, NOT).
Phase 3: Data Management
Once you have data saved in a database, it needs to be managed. This is because data will need to be constantly changed using CRUD.
What does CRUD stand for?
- C - Create
- R - Read
- U - Update
- D - Delete
Common formats that allow data to be exchanged between systems
- Comma-Separated Value (CSV) files
- Extensible Markup Language (XML)
- JavaScript Object Notation (JSON)
What other methods are there to exchange data between people?
- Memory stick
- Optical media
- Removable hard drive
- Paper-based
Craig n Dave Video
Transaction Processing
Transaction Processing
Topic 6: Databases
(6) Transaction Processing
What is meant by the term transaction processing?
A transaction is any information processing that is divided into a single operation. Each transaction must succeed or fail. A transaction can never be partially complete.
What is meant by the term ACID-compliant transactions?
To ensure data integrity, transaction processing in all database management systems (DBMS) must conform to rules. These rules are referred to as ACID. These rules describe the properties required by all database transactions.
What does ACID stand for?
- A - Atomicity
- C - Consistency
- I - Isolation
- D - Durability
What is meant by Atomicity?
Atomicity requires that a change to a database is either completely performed or not at all. A half-completed change must not be saved to the database. This helps to prevent loss of data or data corruption.
How is Atomicity implemented?
Atomicity can be achieved by making all changes to a copy of a file. This ensures that the original copy is not affected until a change is definitely complete. This can also be implemented by keeping a record of transactions in the form of a log.
What is meant by Consistency?
Consistency requires that changes must retain the overall state of the database. For example, if a value is entered under a foreign key, there must be a corresponding primary key value in another table. If a primary key value is deleted, all references to it are removed across the database. This is implemented using referential integrity.
What is meant by Isolation?
Isolation requires that one transaction must not be interrupted by another. The transaction must occur in isolation so other users/processes cannot access the data that is being used by another transaction.
How is Isolation implemented?
Isolation is enforced by using record locking. Record locking allows one user or process to access and modify data at any one time. This means that data being used elsewhere cannot be modified. Only when the transaction is fully complete will be lock be removed. Only when the transaction is fully complete will be lock be removed. Record locking also means the outcome of concurrent transactions is the same as if transactions were completed sequentially.
What is the problem with enforcing record locking?
The problem with record locking is that deadlocks can occur. A deadlock happens when two or more transactions are waiting for a record lock to be removed before they can complete. This causes all activity to halt and remains at a standstill forever until the DBMS detects the deadlock and aborts one of the transactions. For example:
- Transaction A is using rows in the Accounts, but needs rows in Orders to complete.
- Transaction B is using those very rows in the Orders, but needs the rows in Accounts to complete.
- Transaction A and B can’t complete because they need records locked to another transaction.
What is meant by Durability?
Durability means that once a change has been made to a database, it must not be lost due to a system failure to a power cut.
How is Durability implemented?
To implement Durability (i.e. changes are not lost because of a power cut/system failure), we ensure the database writes completed transactions to secondary storage quickly. We don’t save data long term in main memory because it is temporary and would be lost if the power turned off/system failed.
Craig n Dave Video
Topic 7: Networks
Compression
Compression
Topic 7: Networks
(1) Compression
What is compression?
Compression reduces the amount of storage space that a file takes up. The dimensions of the file (e.g. image size of sound duration is not changed).
Why is compression used?
- Reduce the file size. This therefore reduces space on disk / servers. This is also useful as most people have limited data allowances on their mobile data.
- Reduce the amount of time it takes to download and upload data.
- Reduces buffering as the data packets being sent / loaded are smaller.
- Voice can be transmitted fast enough to keep up with speech
What is meant by the term lossy compression?
Lossy compression PERMANENTLY removes some data from the file. It tries to reconstruct a file without the missing data. Lossy compression creates much smaller file sizes but some loss of quality.
How does lossy compression work?
It tries to REMOVE the least important details of a file that take up storage space. For example if multiple pixels are the same colour they are removed. If a sound file has high frequencies that we can’t hear they are removed.
How lossy compression will affect different types of media
| Media | Can lossy be used? | What might the file be like after lossy compression? |
|---|---|---|
| Images | Yes | The quality of the image will be reduced. It will most likely look pixelated. |
| Sound | Yes | The quality of the sound will be reduced. |
| Text | No | It cannot be used because it would have to remove text, therefore making the text file difficult or even impossible to read. |
What are the benefits and drawbacks of lossy compression?
| Benefits | Drawbacks |
|---|---|
| Can create very small file sizes. | The quality of the file degrades significantly the more compression you do. |
| You cannot get the file back to the original after compressing. |
Diagram of lossy compression
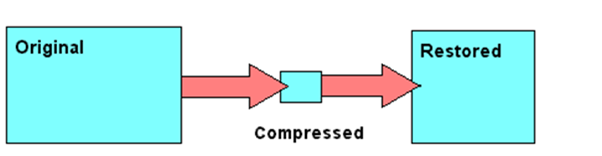
It has significantly removed the file size. The restored file has lost data that cannot be restored.
How does the number of colours affect the file size of an image?
For each colour used in an image, this colour needs to be stored. Using more colours in an image means a larger number of bits will be needed per pixel to represent each colour.
Example 1
In this example, the only colours used by the image are black and white. This means only 1 bit per pixel is needed:
- 0 can be used to represent black.
- 1 can be used to represent white.
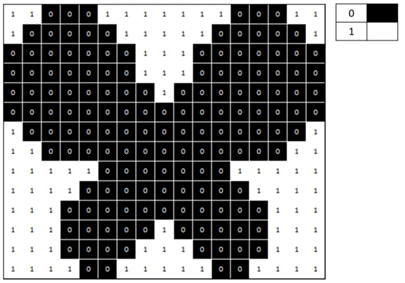
Example 2
If four colours are needed, 2 bits are required per pixel:
- 00 represents black
- 01 represents blue
- 10 represents green
- 11 represents white.
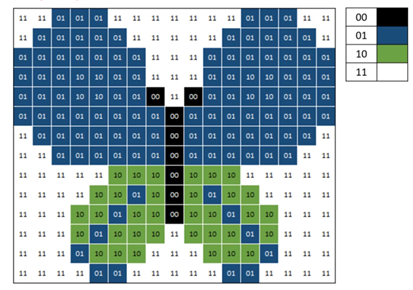
In this example, how many bits are required per pixel?
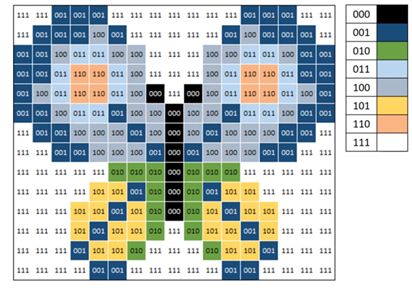
In the above example, 8 colours are used. To represent 8 different colours in binary, we need enough bits to represent each different colour. In denary, 7 = 111. That is 3 bits. 0-7 gives us 8 different combinations of 1s and 0s. That is enough to represent each different colour. This means 3 bits are needed per pixel for 8 colours.
What would be the file size of the above image in bytes? Show your working.
The above image is 17x14 pixels. Each pixel is 3 bits. Therefore, the file size is:17x14x3 = 714bits / 8 = 89.25 bytes.
How could lossy compression be used to reduce the file size of an image?
Lossy compression could be used to reduce the number of colours stored. This means a lower number of bits per pixel is needed to represent all the possible colours. This type of compression will permanently remove the colours from the image. This does result in a loss of quality, but this is often acceptable.
What is meant by the term lossless compression?
Lossless compression makes the file smaller but DOES NOT PERMANENTLY remove data from the file. It will creates smaller file but not as much as Lossy Compression.
How does lossless compression work?
It works by looking for data that is repeated in the file. If there is repeated data it is only stored once.
Where can lossless be used?
| Media | Can lossless be used? |
|---|---|
| Images | Yes |
| Sound | Yes |
| Text | Yes |
What are the benefits and drawbacks of lossless compression?
| Benefits | Drawbacks |
|---|---|
| No loss of quality. | The file sizes are larger than those that would have been created by lossy. |
| You can return the file back to its original after compression. |
Diagram of lossless compression
The compressed file has removed data, although not as much as lossy. The restored file has not lost any data.
Example
In this example, the image has 8 colours. This requires 3 bits for each of the 238 pixels on the image. This results in a total file size of 89.25 bytes. Lossy compression could be used to remove colours from the image, but this would permanently lower the quality. We could not restore the image to the original level of quality.

Instead of storing 3 bits for each of the 238 pixels, we can compress the data by storing the binary value of each colour once, followed by the number of times it appears in a row.
For example, if the first row contains 7 white pixels, we normally store "111" for each one (totalling 21 bits: 111 111 111 111 111 111 111). With lossless compression, we store "111" just once, followed by "111" (the binary for 7). This reduces the storage to just 6 bits (111 111) while keeping the original image quality intact.
Craig n Dave Video
Encoding
Encoding
Topic 7: Networks
(2) Encoding
In the previous lesson, you learned about lossy and lossless compression. In this lesson, you will learn about two methods of lossless compression. Both methods allow us to compress files bu tthen allow us to restore the file back to its original quality
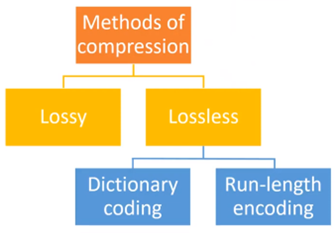
What is dictionary coding?
This is a way of lossless compression of text. It will build up an index table that is then used to reconstruct the data back to its original form. It will look for words that are repeating and then stores them once and gives them an index number. Then every time the same word is used again, the index will be used instead of the repeated word.
What will be stored in the compressed file?
- The dictionary index
- The sequence of ccurences needed to recreate the original data
Example of dictionary coding
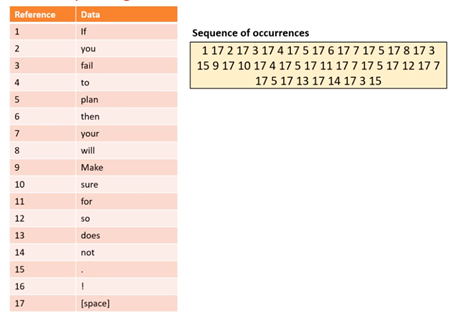
“If you fail to plan then your plan will fail. Make sure to plan for your plan so your plan does not fail!”
How did dictionary coding reduce the storage space?
The original message has 105 characters, including spaces. Assuming that ASCII (8 bits) is used (8 x 105) then this will be stored as 840 bits.
After compression, we have 46 numbers in the sequence in the sequence. As we need to store the numbers 1 to 17 we need 5 bits: 00001 = 1. 10001 = 17. Now we only need 5 bits. 5 x 46 = 230 bits.
Therefore, the file size has been reduced from 840 bits to 230 bits.
Example of dictionary coding
“To the swinging and the ringing of the bells, bells, bells-
Of the bells, bells, bells, bells Bells, bells, bells-
To the rhyming and the chiming of the bells!
How did dictionary coding reduce the storage space?
The original message has 155 characters, including spaces. Assuming that ASCII (8 bits) is used (8 x 155) then this will be stored as 1240 bits.
After compression, we have 41 numbers in the sequence in the sequence. As we need to store the numbers 0 to 12 we need 4 bits: 0000 = 0. 1100 = 14. Now we only need 4 bits. 4 x 41 = 164 bits.
Therefore, the file size has been reduced from 1240 bits to 164 bits.
What is run-length encoding?
This is a way of lossless compression of bitmap images. It will look for continuous pixels that are the same. Instead of storing the same binary code for each repeated pixel, it is stored once.
Why would run length encoding work well on this image?

There are a lot of repeated pixels. In particular, there are a lot of black pixels and therefore storing each one will be very inefficient.
Example of run length encoding
Here is a 10 pixel x 10 pixel image. W indicates a white pixel. B indicates a black pixel. Reconstruct this image using the encoded data.
What will be stored in the compressed file?
Frequency/data pairs – This will state the data (e.g. binary value) and then now many times it occurs. For example, 22/0000 would indicate 22 white pixels.
Craig n Dave Video
Encryption
Encryption
Topic 7: Networks
(3) Encryption
What is encryption?
This is a process of converting data (plaintext) into an unreadable form (ciphertext). The data is turned into an unreadable form using an algorithm and a unique key. Encryption means that data can only be read by the sender and the intended recipient.
Does encyption mean you cannot be hacked?
No. Encryption doesn’t stop you from being hacked but it will make any of the stolen data unreadable unless you have the decryption key.
What is symmetric encryption?
This is when a single key is used to both encrypt AND decrypt data. When using this method, both the sender and recipient of the data need to know the key – and both parties need to keep it secret. The same key can be used multiple times, but it is more secure to generate a new key each time.
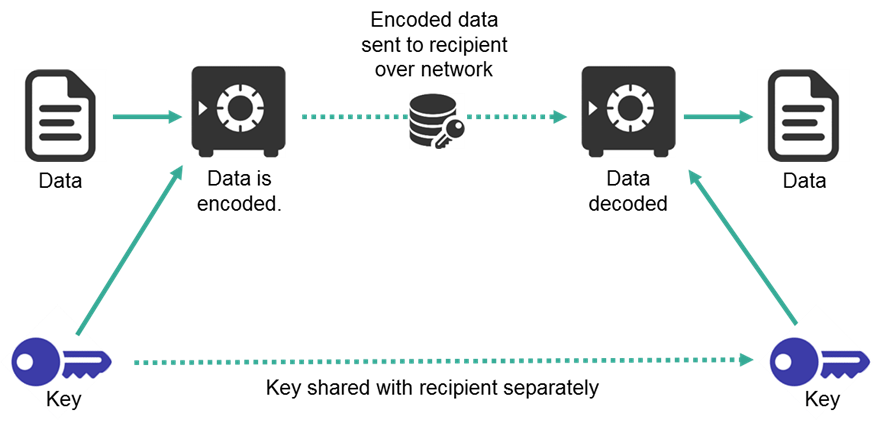
What is a problem with symmetric encryption?
There is a risk that the encrypted data can be decrypted and accessed by an attacker if:
- The key is intercepted when it is being sent.
- The key production process is repeated to acquire a copy of the key.
Therefore, this method of encryption is rarely used for sensitive information such as payment card details.
What is asymmetric encryption?
Asymmetric encryption uses two separate keys:
- The first key (public key) encrypts the data.
- The second key (private key) decrypts the data.
We start with the unencrypted data and encrypt it using the public key. Once the message is sent, the recipient decrypts the data using the private key.
What is meant by a key pair?
Asymmetric encryption uses two keys. One of the keys is chosen to encrypt the data (public key). The other key is chosen to decrypt the data (private key). Together, these keys form what is called a key pair.
What is the difference between the public and private key?
The public key is used to encrypt the data. The private key is used to decrypt the data. The public key can be made public, so it can be given out or even published online. Whereas the private key is never sent to anyone. It should only ever be known by the intended recipient of the encrypted data. The intended recipient gives out their public key which allows other people to encrypt data so it can be sent back to them securely.
How does asymmetric encryption work in practice?
- John has a key pair: a private key and a public key. He wants Jane to be able to send him data securely. And he wants to keep his private key secret.
- To achieve this, John will give Jane his public key.
- Jane will encrypt the data using John’s public key (which he sent her).
- John would then use his private key (which has never been sent to anyone) to decrypt the data.
- John doesn’t need to worry about someone intercepting the encrypted message. They can’t decrypt it without the private key, which has been kept safe and never sent out.
- The private key was never shared so there is little risk it could be accessed by an attacker.
Why is asymmetric encryption preferred?
Asymmetric encryption is much more secure because it uses two keys instead of one. Even if you have access to the public key, you cannot decrypt the data without the private key. The private key doesn’t need to be given out or sent over the internet. The recipient already has it. This reduces the risk that it can be accessed by an attacker. Additionally, it is virtually impossible to derive one key from another. This also makes asymmetric encryption more secure.
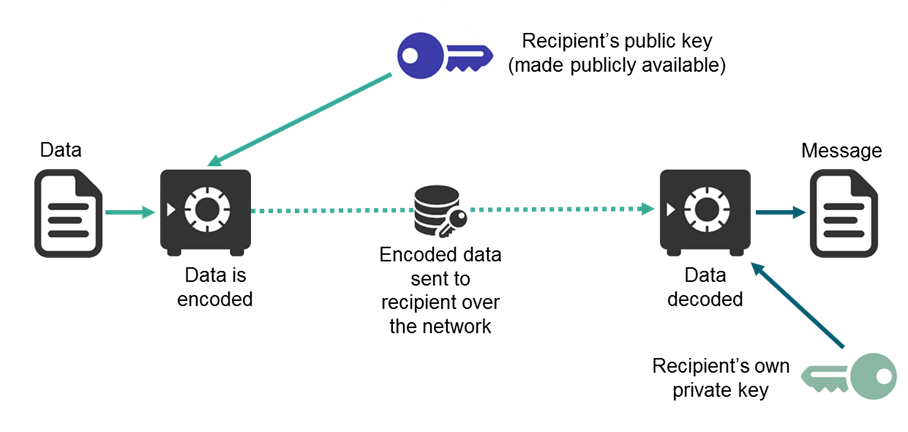
Why is asymmetric encryption better suited to transactions over the internet than symmetric encryption?
Symmetric encryption requires both parties to have a copy of the key. That key can be used to encrypt AND decrypt the data. The key would need to be sent over the internet, so an attacker could intercept it.
• Asymmetric avoids the requirement to send the key over the internet. There are two different keys:
- The public key encrypts the data. This key can be distributed online.
- The private key decrypts the data and this is kept private and is not sent over the internet. Only intended recipient already has it. This reduces the risk it could be accessed by an attacker when it is being sent.
When might it be useful to use the private key instead of the public key to encrypt data?
If a private key is used to encrypt data, anyone could decrypt it using the public key that has been made available to everyone. This is useful if you want to be certain about the identity of the person who sent the data. The fact that the message can be decrypted with the public key means the data must have originally been encrypted by the person with the private key. Therefore, the sender of the data can be confirmed as authentic.
What is meant by a combined encryption key?
This is when the sender uses both their private key AND the recipient’s public key to encrypt the data. For example, John would use his private key to encrypt the data and then Jane’s public key to encrypt the data. The ciphertext is then sent to Jane. To decrypt the message, Jane would use her private key and her copy of John’s public key.
What are the benefits of using a combined encryption key?
- The sender and recipient can be sure that nobody else has read the message.
- The intended recipient can be certain who sent the message.
- There is no risk the message could be intercepted a changed.
Craig n Dave Video
Hashing
Hashing
Topic 7: Networks
(4) Hashing
What is hashing?
Hashing (also known as a hashing function) transforms a string of characters into a fixed length hash value that represents what was originally hashed. As the hashed value is generated using the entire input message, even a slight change produces a totally different hash value. The hashed value cannot be reversed back to the original data. Popular hashing algorithms are SHA-1 and MD5.
How is hashing different to encryption?
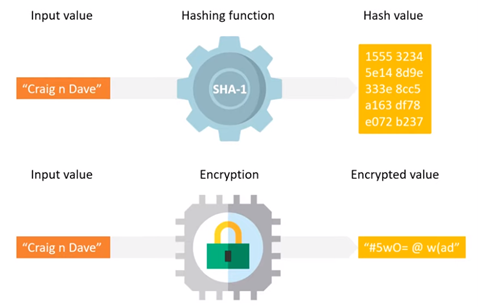
Hashing is a one-way process. You cannot get the original value back from the hashed value. Even if you access the hashing function, you cannot get the original data back. Encryption is a two-way process. If you have access to the key(s) you can convert the data back to its original form.
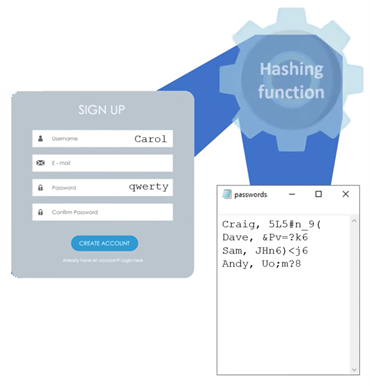
Why are passwords and PINs commonly hashed?
To prevent passwords and PINs being read by a hacker. Therefore, if accessed by an attacker, they cannot obtain the passwords or PINs. These are never displayed on the screen. If you forget these, you will have to reset them rather than getting a notification about what they are. Once they are reset, they are rehashed and resaved.
What happens when you login to a website and enter your password?
Hashed passwords are stored. Then when you log into a website, your password is rehashed and then compared against the hashed password stored. If the two match access is granted.
Craig n Dave Video
LANs & WANs
LANs & WANs
Topic 7: Networks
(5) LANs & WANs
What is meant by the term 'standalone computer'?
If it is standalone it cannot communicate with any other computers.
What is meant by a network?
A network is two or more computers connected together.
What are the key advantages and disadvantages of networking computers together?
| Advantages | Drawbacks |
|---|---|
| Sharing resources such as printers saves money. | Purchasing the network hardware is expensive |
| You can access your files from any computer in the network. | Managing a large network is complicated. |
| Data is easy to back up as it is stored centrally on the server. | Viruses may be able to infiltrate the network and infect every computer. |
What are the characteristics of a LAN?
- Computers are within a local geographic area and in close proximity to each other.
- MAC addresses are used to transfer data from one computer to another.
- The hardware that is used to make up the network is owned by the organisation.
What are the characteristics of a WAN?
- Computers are NOT close together.
- A router is needed to connect devices together.
- IP addresses are used to transfer data from one computer to another.
- The hardware that is owned to connect devices is owned by a third party.
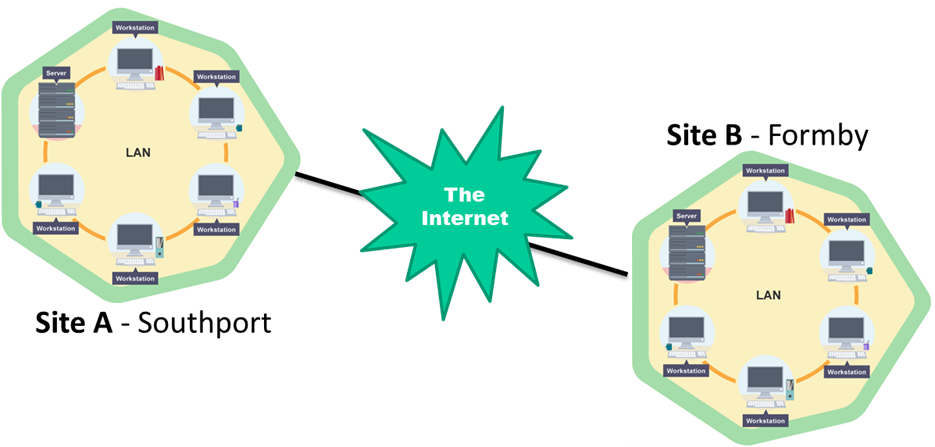
Craig n Dave Video
Network Hardware
Network Hardware
Topic 7: Networks
(6) Network Hardware
What is a server?
The server is a powerful computer that will provide single/multiple services to all of the computers on a network.
Examples of servers
- A file server holds all the data files so needs can be accessed by network users.
- A web server will store websites so that they can be accessed by users.
- A print server may organise printing on different printers by multiple users.
What is an NIC?

Network Interface Card
Where can the NIC be found?
This is built into a computer.
What device does the NIC connect to?
This connects the computer to a switch using a cable.
Each NIC has a MAC address. What is meant by the term MAC address?
Each NIC has a unique MAC address – Media Access Control. This enables devices to be recognised on the network. It means that data can be sent from the server to the correct MAC address. No two NICs have the same MAC address.
What is a Switch? What does it do?

A switch connects devices together in an Ethernet network. A switch:
- stores the MAC address of each device connected to it.
- receives and examines the incoming data packets from devices.
- forwards the data packets onto other computers/ MAC addresses.
What information about every NIC will the switch store? Why?
The NIC will store the MAC address of every NIC/WNIC that is connected to the switch. Therefore when the switch receives data from the server, it will switch/direct the data packets to the correct MAC address.
Diagram showing how NICs connect to the switch and then the server
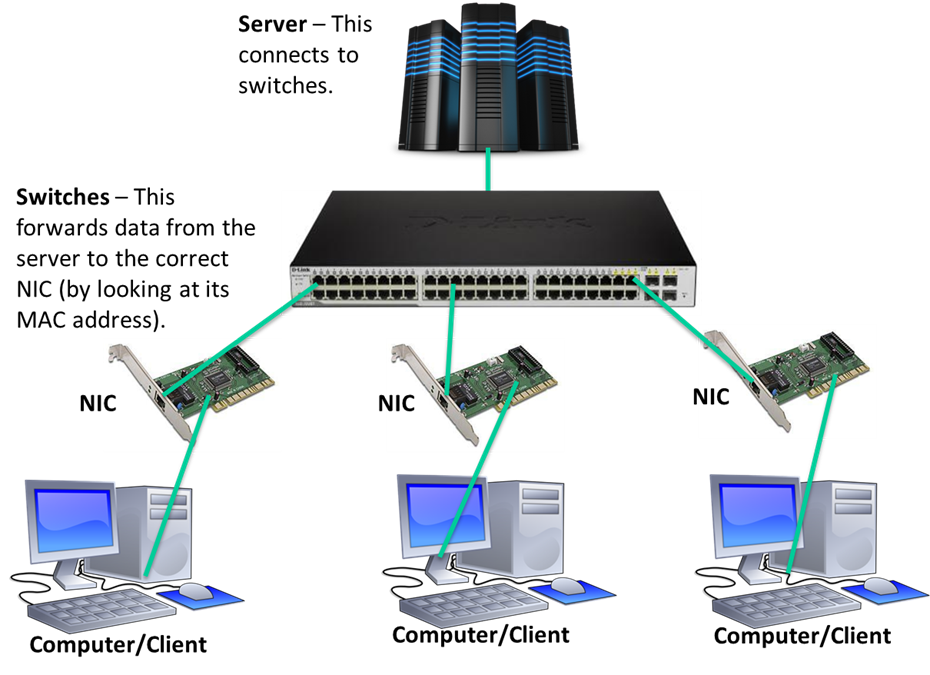
A hub is similar to a switch. What is the main difference between a hub and a switch.
A hub will send data packets to all devices on the network. If the packets are not intended for a device, they will ignore it. A switch will only send data packets to a single device.
What is meant by the term modem? What does it do?
A modem transforms digital information from your computer into analogue signals that can be transmitted through wires. It can also translate incoming analogue signals back into digital data that your computer can understand.
How does a modem work?
A modem works by modulating and demodulating electrical signals sent through phone lines, coaxial cables and other types of wiring. Most modems only have two ports:
- One that connects to the outside world.
- An Ethernet port that connects to a computer or router.
What is a router? What does it do?
A router will connect your computer to another computer in a different network. Often it is used to connect your computer to the internet. A router:
- Gives each device connected to it an IP address.
- Receives and examines the incoming data packets from devices.
- Forwards the data packets to other devices.
When might you use a router?
- To connect a computer to the internet.
- To connect a LAN to a WAN or to connect a LAN to another LAN.
What does a router use to connect networks together?
It does not use MAC addresses. Instead it uses IP addresses. Each network will be given an IP address and therefore when you want to connect to another network, it will route you through to its IP address.
What is a WAP? What does it do?

Wireless Access Point. This will allow devices to communicate wirelessly. Devices can therefore connect to the switch wirelessly. A WAP will:
- Receives and examines the incoming data packets from devices.
- Forward the data packets to other devices.
How does the WAP send and receive data to / from devices using a WNIC?
A WNIC is a wirelss network interface card. The WNIC will send out radio waves/data packets which are then received by a Wireless Network Interface Card (WNIC). It will also receive radio waves/data packets from WNICS.
Diagran of a network layout
This network has four computers which connect to a server through a wired connection. Each computer has internet access. The company has a wireless connection for staff to connect their mobile devices.
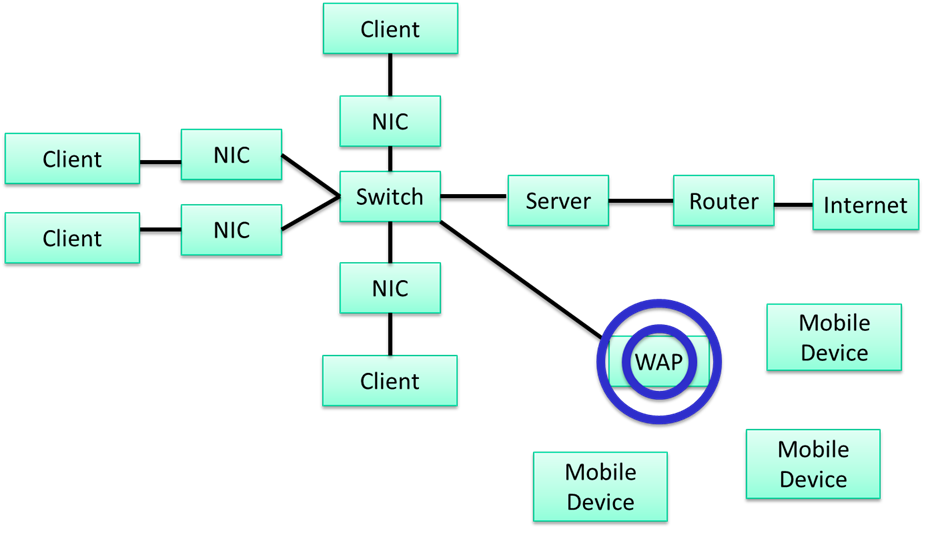
What is meant by the term transmission media?
This is the method that is used to transfer data from one computer to another.
With physical, wired connections, there are many cable choices available. What are the three most popular?
- Twisted pair cables (copper)
- Coaxial cables (copper)
- Fibre optic cables
What is meant by a twisted pair cable?
This is a cable made up of insulated copper wires. Twisted pair cables are more affordable than using coaxial and fibre optic cables.
What are twisted pair cables typically used for?
- Telephone networks
- Data networks
- Cable shielding
What is meant by a coaxial cable?
This is a cable made up of four cylindrical components. From the inside to outside of the cable:
- A solid conductor wire.
- A layer of insulation.
- A grounding conductor.
- A layer of exterior insulation.
What are coaxial cables typically used for?
- Feedlines that connect radio transmitters and receivers to antennas.
- Computer network connections
- Digital audio and cable television
What is meant by a fibre optic cable?
This is a cable made up of very thin optical fibres bundled together in a single cable. The fibres can either be glass or plastic.
What is a fibre optic cable typically used for?
Fibre optic cables are used for long distance connections between cities, countries, data centres and organisations transmitting a large volume of data.
Advantages and disadvantages of copper cables
| Advantages | Disadvantages |
|---|---|
| Relatively good bandwidth | Signal is affected by electric and magnetic fields. |
| Relatively inexpensive | Very heavy cables. |
| Low error rate - it's been tried and tested. | Cable length is limited to 100m. |
Advantages and disadvantages of fibre optic cables
| Advantages | Disadvantages |
|---|---|
| Very good bandwidth | Expensive to buy and install. |
| Low loss of signal over distance | If the glass fibre breaks, then they cannot be repaired. |
| Not affected by electric or magnetic fields. | Expensive optical transmitters and receivers are needed. |
| Require very little power. | |
| More difficult to tap into than copper cables. |
Advantages and disadvantages of wireless
| Advantages | Disadvantages |
|---|---|
| Safer because there is no need for trailing wires. | Less bandwidth than a wired connection |
| Allows devices to be used anywhere within signal range. | Signal can be blocked by objects or walls. |
| Easier to add devices to a network than with a wired connection. | More security issues because data is transmitted using radio waves. |
Client Server v P2P
Client Server v P2P
Topic 7: Networks
(7) Client Server v P2P
What is meant by the term 'client server' network?
This is a network where all of the devices are connected to a server, often via a switch. The server has overall control of the network.

In a client-server network, what is the role of a server?
The server is a powerful computer that will provide single/multiple services to all of the computers on a network. Role:
- The server waits for requests from a client.
- Acknowledges the request.
- The requested data is sent back to the client.
- The server may need to pass the request (e.g. for a web page) to another server – in which case, it becomes the “client.”
In a client-server network, what is the role of a client?
A client is a computer which requests services or resources from the server. Role:
- The client sends requests to the server.
- The client then waits for a reply.
- The client receives the reply.
Advantages and disadvantages of client server networks
| Advantages | Disadvantages |
|---|---|
| Software installed once on one server can be done automatically on others – e.g. anti-virus, firewalls etc. | This network needs an expensive server (as they require large disk space and memory) and a networking operating system. |
| The user does not need to do any management of the computer. There is usually a network manager. | A network manager is usually required – increased wage bill. |
| Network processing is done centrally not at individual computer. Therefore you can access your data from any computer. | There is a reliance on the central server. If it fails the whole network does not work. |
| Backups can be processed quicker. All the data is in a central place on the server. |
What is meant by a peer to peer network?
In this type of network, all of the computers have equal status. There is no overall device that have overall control of the network (e.g. there is no server.)
What is meant by the term 'peer'?
A peer is simply a computer in network that has the same status as every other computer. In a client server network, the computers are called clients instead.
Advantages and disadvantages of peer to peer networks
| Advantages | Disadvantages |
|---|---|
| Only normal computers are required. There is no need to purchase an expensive server. | The user may have to use the same computer each time to access the same data they did previously. |
| Each user manages their own computer. This means there is no need for a network manager. | Data can be stored on any computer so there is less organisation. Backups cannot be don’t centrally. |
| Easy to Setup. Set-up can be done via wizards within software. No technical knowledge is required. | Software has to be installed on each computer. Security, anti-virus and backup are all done individually. |
| There is no reliance on a central control – less to go wrong. | Viruses and malware are easily transferred over this type of network (cant have central management of security.) |
Differences between client server and peer to peer networks
| Item | Client-Server | Peer-to-Peer |
|---|---|---|
| Storage of files | A central backing store is available to all computers | Storage facilities are distributed across all computers |
| Security | Security is controlled by the central computer | Security is not centrally controlled |
| Ease of backups | Backups are done centrally on the server | Backup must be done separately for each computer |
| Reliance | All users are reliant on the central server | No central server |
| Where it's used | Can support hundreds or even thousands of users and grow with an organisation | Easy to set up but most suited to homes and small businesses |
Craig n Dave Video
Protocols & Standards
Protocols & Standards
Topic 7: Networks
(8) Standards & Protocols
What is meant by the term 'standard'?
This is an agreed way of doing things. Standards allows hardware and software by different manufactures to interact with each other.
Examples of standards
- Ethernet
- Bluetooth
- Wi-Fi
- Comma Separated Value (.CSV) files
- Text files (.txt)
What is a protocol?
This is a set of rules for communication. Computers use protocols to ensure that data can be transferred from one computer/network and be understood by another.
Internet Protocols
| Transmission Control Protocol Internet Protocol (TCP/IP) | Used to send data packets over the internet. TCP - This part, breaks up messages to be sent over the internet into smaller packets, reassembles the packets and detects errors & resends lost messages. IP - This part, is responsible for packet switching. |
Website Protocols
| HyperText Transfer Protocol (HTTP) | It is used for accessing and receiving web pages.The protocol requests the web server to load the requested web page to the user’s browser for viewing. |
| HyperText Transfer Protocol Secure (HTTPS) | This is a safe version of the HTTP protocol. HTTPS encrypts the information so that it cannot be understood if it is hacked. |
Diagram of the HTTP protocol
File Transfer Protocol
| File Transfer Protocol (FTP) | It is used to access, edit and move files between devices on a network.For example, the client may request for data from the server. Therefore, to get your data off the server to your computer the FTP protocol is used. |
Email Protocols
| Simple Mail Transfer Protocol (SMTP) | Email have to be stored on a Mail Server. Gmail will store their emails on their own mail server and Yahoo will store their emails on their own mail server. Therefore SMTP is used to transfer emails from one mail server to another mail server. |
| Post Office Protocol (POP) | Used to download emails from a server. The server holds the email until you download it, at which point it is deleted form the server. If this is used then the mail can only be read on one device. |
| Internet Message Access Protocol (IMAP) | IMAP will sync the email from the server, however and will leave the message on the server until you officially delete it. This means other devices checking the same mailbox will also see the messages. |
Example showing where SMTP, IMAP and POP are used
Bob sends an email from his Gmail account to Alice who has a Yahoo account.
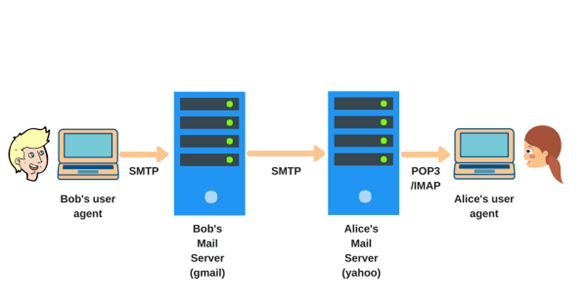
Craig n Dave Video
Internet Structure
Internet Structure
Topic 7: Networks
(9) Internet Structure
What is meant by the term internet?
The internet is a network of computer networks. It’s basically the hardware that connects computers together across the world. In order to pass data through the internet each network has to use the same TCP/IP protocol.
Difference between the internet and the world wide web (WWW)
The internet is only the networking hardware that connects lots of computers / networks together.
The world wide web is a service that runs on the internet. It is a collection of websites that are stored/hosted on servers. Therefore we use the internet to connect to the server that a website is stored on.
What is hosting?
When you make a website, it needs to be stored somewhere so that it can be accessed by its users. Websites cannot be stored on ‘normal’ computers. Instead they are stored on webservers.
Hosting is when a website is stored on a webserver. Then when you want to access a website, your computer will then become the client and request the website service from the webserver.
What are the features of hosting websites?
- The website to be accessible 24/7/365 by everyone.
- Allow multiple users to access the website at the same time.
- The website to have greater security.
What is DNS and what is it used for?
It stands for Domain Name System. It works like this:
- DNS technology allows you to type a URL such as google.co.uk into your web browser.
- It translates the URL google.co.uk into an IP address
- e.g. www.google.co.uk = 74.125.131.94.
- You are then connected to that IP address and NOT the website name.
What are the steps involved in DNS?
- User enters URL into the browser – e.g. www.bbc.co.uk
- URL is sent to a Name Server as a DNS query.
- The name server will return an IP address to the browser – e.g. 212.58.244.18
- The browser will then send a request to the IP/webserver. The webserver will then process the request. The webserver will then return the webpage/data/file.
- The data is then loaded onto the screen, usually in the form of a website.
What happens if the DNS cannot find the IP address?
If DNS cannot find the IP it passes request to higher DNS. It is still cannot find it then it will return an error to the browser.
Diagram showing the TCP/IP stack
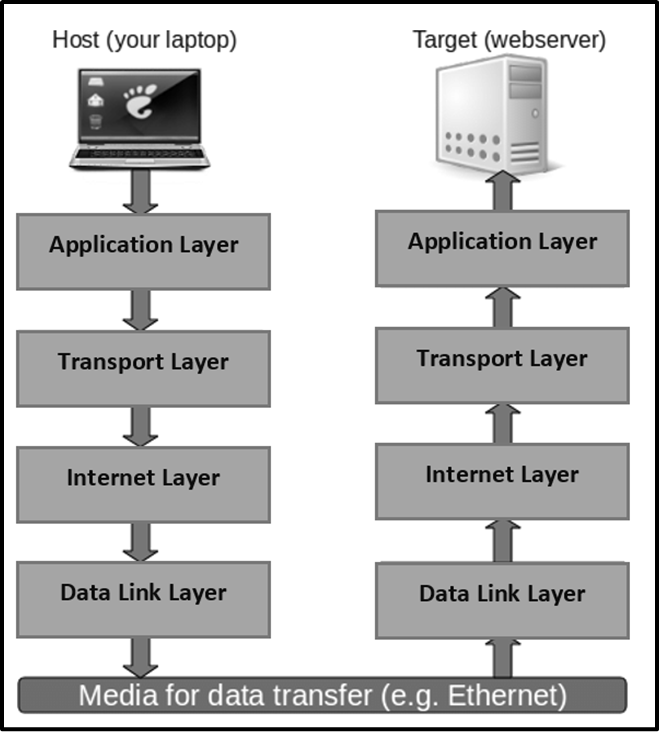
What do each of the layers in the TCP/IP stack mean?
| Layer | Description |
|---|---|
| Application Layer |
|
| Transport Layer |
|
| Internet Layer |
|
| Link Layer |
|
What is meant by the term protocol layer?
We use layers to reduce the complexity. Layers breaks down the network into manageable sub-problems.
What are the benefits of layers in protocols?
- A layer can be removed/changed without affecting any other layers.
- Each layer has its own purpose and is self-contained so it does not need to consider what the other layers do.
- Hardware manufactures can make hardware to fit in one layer.
What is packet switching?
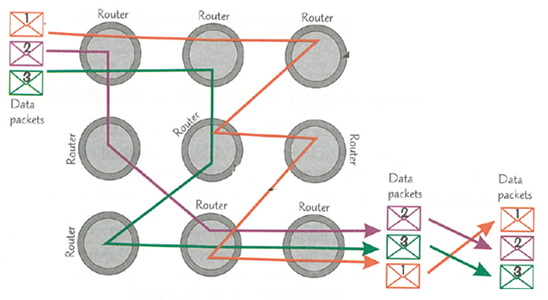
This is when the data is broken down into chunks called packets. The packets have labels including the IP address being sent to and the order of the packet in the complete message. Each packet is sent via the most convenient / least congested route, which may be different for each packet. This means they may arrive in a different order to which they were sent. Once the packets arrive at receiver they are reordered. It checks for errors and lost packets are individually resent.
What are the stages of packet switching?
- Split the data into equal sized blocks called packet
- Each packet is given a label of information (including the destination IP address and the order of the packet in the complete message).
- Each packet is placed on the network and each may travel a different route.
- At each note on the network, the destination address is read and the best route is found.
- The packets then travel down the different routes.
- The packets will then arrive out of order so need to be put together again in order.
- Check for errors and lost packets are sent again.
When would you use this?
When you are transferring or downloading data that does not need to be viewed in real-time or is not continuous.
What are the benefits and drawbacks of packet switching?
| Benefits | Drawbacks |
|---|---|
| It does not waste bandwidth as it’s not all used up with one connection. | Packets can take different routes so may arrive in the wrong order. Time is spent reassembling them. |
| If there is an error, only one individual packet needs to be resent rather than the whole data. | Data can become easily corrupted during transmission. |
| More secure. Big files can be sent as a collection of small packets down different routes making them more difficult to intercept. | Not suitable when you are steaming data that needs to be viewed in real-time. |
What is circuit switching?

This will create a temporary dedicated link of bandwidth between the source and destination that lasts until the transmission is complete.
When would you use this?
When streaming continuous data in real-time such as video.
Benefits and drawbacks of circuit switching
| Benefits | Drawbacks |
|---|---|
| As the bandwidth is dedicated, the quality can be guaranteed. | It can waste a lot of bandwidth as it will reserve bandwidth that never gets used. |
| Data will arrive in the correct order. You don’t need to wait for packet switches or to put packets in order. | Once a channel is used, it cannot be used by another connection. |
Differences between circuit switching and packet switching
| Circuit Switching | Packet Switching |
|---|---|
| Dedicated hardware resources are taken up maintaining a constant connection. | Hardware is used for multiple different connections. |
| Data is sent in one continuous stream. | Data is sent as small discrete packets of data |
| Data is sent along one route. | Data is sent along multiple different routes |
Craig n Dave Videos
Network Threats
Network Threats
Topic 7: Networks
(10) Network Threats
Reasons why someone might carry out a cyber attack
What is meant by the term hacker?
A hacker is a person who attempts to gain access to a computer system with the intent of damaging data or somehow harming that system. Hackers come in many forms – not all hackers have malicious intent.
What is a black hat hacker?
A black hat hacker is a malicious hacker that attempts to gain access to steal data or cause damage.
What is a white hat hacker?
A white hat hacker (also known as an ethical hacker) is a security expert employed by a company. They use their expertise to try and find vulnerabilities so they can be fixed. White hat hackers are paid for this service.
What is a grey hat hacker?
Grey hat hackers are not employed by the company, but they still attempt to locate flaws in a computer system as a hobby. Whilst what they do is technically illegal because there is no permission for what they are doing, they typically inform the company of the flaw so they can fix it.
What is Malware short for?
Malicious Software
Examples of malware
- Viruses – It is capable of copying itself and spreading throughout a system. Viruses can cause damage or steal files. They can’t spread from one computer to another without human action (such as downloading it).
- Worms - These are capable of spreading from one computer to another without human intervention.
- Scareware – Falsely tells you your computer is broken to get you to pay money for it to be ‘fixed’.
- Ransomware – This locks and encrypts all of your files until you pay a large sum of money.
- Spyware – Monitors what keys you are pressing.
- Trojan Horses - A piece of software that looks like genuine software. The user opens the software thinking its genuine and then the infected file is released.
Ways that malware could get on your computer
- One person may send an infected file via email.
- One person may send an infected file via a memory stick.
What is social engineering?
Social engineering involves manipulating a person to giving out private information, access to a restricted system or money.
Social engineering scams lure users into exposing data, spreading malware or providing access to a system. For example:
- Baiting
- Scareware
- Blagging
- Phishing
- Shoulder surfing
- Vishing
- Quid pro quo
What is a phishing email?
Phishing is when a criminal sends you an email pretending to be someone you can trust to trick you into giving out sensitive or personal information.
Example of phishing
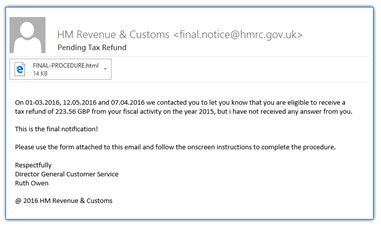
Clues:
- No greeting – The phishers don’t know your name – just your email address, so the greeting is not personalised
- Sense of urgency – Criminals try to persuade you that something bad will happen if you don’t act fast
- Forged link - The link looks genuine, but it may not link to the website given. It will link to a form to hand over personal information.
- Poor spelling & grammar
What is a brute force attack?
In a brute force attack, a hacker will go through ‘trial and error’ in order to try every single possibility of a password until access to an account is gained.
What is a Denial Of Service (DoS) attack?
A DoS attack attempts to flood a website / email server with an overwhelming amount of data requests therefore causing it to crash. Often they will use all of the company bandwidth so customers cannot access the site.
What are the steps involved with a DoS Attack?
- An attacker will send requests to other computers known as zombie/bot computers.
- The (Hundreds/ Thousands of) zombie/bot computers will then send data to a website at the same time.
- The website simply cannot cope with all of the data and will therefore crash causing the website to go ‘down.’
What is the impact on companies if they are victims of a DoS attack?
- Loss of business – both directly while the site cannot be accessed and long term as some may not use the service due to security concerns.
- Bad reputation – the business may gain a bad reputation as customers may have concerns about how seriously they take security.
Two ways that data can travel on a network
- On a wired (Ethernet) network data travels through wires in packets.
- On a wireless (Wi-Fi) network data travels wirelessly in packets.
What is data interception?
Data Interception is reading the data packets while they are being transferred from one computer to another computer. For example, logins, passwords, credit card numbers and PIN numbers.
What is a database and why is SQL used?
Large companies will use databases to store their users details (e.g. Facebook etc). In order to search these databases SQL may be used. When the user types in their username and password for example then the SQL will check that these details are correct in the database before giving them access.
What is meant by the term SQL injection?
Criminals can input specifically created SQL commands instead of a username/password to bypass the login requirements and gain access to the database so that the criminals have access to the data.
No SQL injection

With SQL injection

Craig n Dave Video
Threat Prevention
Threat Prevention
Topic 7: Networks
(11) Threat Prevention
What is meant by the term physical security?
This is actual hardware that is setup to prevent someone accessing computer devices. This will stop them from accessing the data on the devices or from stealing them.
Examples of physical security
- Locks on the doors
- Security guards
- CCTV
- Burglar alarms
- Window bars / grills
Which ones from the above would not actually stop data/hardware from being stolen?
- CCTV
- Burglar alarms
Why is physical security not enough on its own?
The problem is that an attacker does not even need to touch the hardware to be able to attack it. Attackers can carry out attacks on computers hundreds of miles away.
Why should people have anti-malware software installed on their computer?
It is software that sits and runs in the background. It will constantly scan every single piece of data that accesses your computer (e.g. via the internet or memory stick). It will compare all the data against a database of known malware and if it detects malware it will bring this to your attention.
Anti-malware often has automatic updates installed. What is meant by automatic updates?
This is when the database of known malware is updated automatically, often each day.
Whhat happens if you have automatic updates disabled?
The database of known malware would not be updated. Therefore, your anti-malware software would not be able to detect new malware.
"Anti-Malware stops hackers". True or false?
False, it only detects malicious software, not unauthorised access. Firewall software will stop this.
What is meant by the term proxy?
A proxy is a physical device placed between a network and a remote source. All traffic travels through the device on its way into and out of the network. A proxy ensures there is no direct, physical connection between a single user and a remote source.
Describe how a proxy might be used?
- A proxy could be used to handle web page requests. If the page is not on the proxy’s banned list, it will pass on the request.
- A proxy can also look at the page and its contents and choose whether or not to pass it to the user.
What is a firewall?
A firewall is software that checks all incoming traffic from the Internet or a network BEFORE it reaches your computer. Based on the settings in place, if it detected authorised access, it will block access.
How does a firewall work?
- It will examine EVERYTHING all requests made to your computer externally (e.g. website visited, email opened etc).
- When it examines a request it will compare it against a list of rules. If the data is within the rules it will grant access.
- If the request is not within the rules (e.g. an untrusted source) it will get blocked.
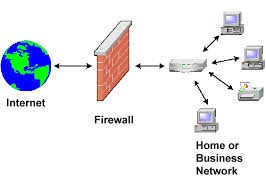
"Firewalls will stop viruses". True or false?
False, it will only stop unauthorised access. You will need antimalware for this.
What is meant by the term 'Access Level'?
An access right will allow different groups/users to be able to access different parts of the network and be denied access to other parts.
What are access levels usually attached to?
Everyone on a network will have a userID (username). Usernames can be placed into different groups (e.g. managers will be in one group). Access levels are usually therefore attached to groups / individual users.
Describe the following types of Access Level
| Read | You can only read the data and make NO changes to it. |
| Write | You will be able to read and make changes to data. |
| Delete | You will be able to delete data. |
| Create | You will be able to create new data and save it. |
What rules should you follow when creating a new password?
- Use a minimum of eight characters. However they can still be guessed by brutal force attacks.
- Use a mixture of numbers, lowercase and uppercase characters.
- Include symbols such as &, !, #, %.
- Do not include your name, DOB or personal details.
- Change your password regularly (every 2 to 3 months).
- Try not to include dictionary words – brutal force attacks can guess these easily.
What is meant by a secure password system?
This is when a network requires a user to choose a password that meets certain requirements. For example, the requirement could be that the password:
- Has a minimum length.
- Upper case and lowercase letters.
- Can’t be the same as your last X passwords.
- Must be changed every Y number of days.
- Can’t contain personal details.
What is a potential problem with implementing strict rules on passwords?
If there are strict password rules, this could make the password difficult to remember for individual users. This can lead to users writing down their passwords and storing them in a place where they could be accessed by a third party, who can then access the network. Writing down the password so the user doesn’t forget it will defeat the object of having a password.
Craig n Dave Video
Topic 8: Legislation & Wider Issues
Data Protection
Data Protection
Topic 8: Legislation & Wider Issues
(1) Data Protection Act 1998
Why was this law setup?
Any organisation that holds personal information MUST follow the Data Protection Act. This act specifies the rules about collecting, storing and using personal and sensitive data.
Examples of personal data
| Personal | Sensitive |
|---|---|
| Name | Nationality |
| Address | Ethnicity |
| Banking details | Political beliefs |
| Date of birth | Biometrics |
| Financial transactions | Sexual orientation |
Those that have data stored about them are known as data subjects. An organisation (data controller) stores personal data about you, what rights do you have?
| Individual Right | What does this mean? |
|---|---|
| Right to be informed | The controller must tell the subject how and why their data will be used. |
| Right to access | The controller must give the subject a copy of their personal data. |
| Right to rectification | The controller must fix any data held about the subject that is inaccurate. |
| Right to erasure (also known as right to be forgotten) | In some situations, the controller must delete data held about the subject. |
| Right to object to direct marketing | The subject has the right to stop the controller from using their personal data for direct marketing. |
| Right to restrict processing | In some situations, the controller must keep a copy of the personal data as it is and not use it. |
| Rights in relation to automated decision making. | The subject has the right to have a human review of decision made automatically that has a legal or similarly significant impact on the subject. |
| Right to compensation | The subject can claim compensation for loss caused by not following the data protection act. |
| Right to complain | The subject can complain to the ICO if the controller doesn’t follow the data protection act. |
If an organisation stores personal data, what eight principles must they follow?
- Data must be processed fairly and lawfully.
- Data must be adequate, relevant and not excessive.
- Data must be accurate and up to date.
- Data must not be kept for longer than necessary.
- Data must only be used for the purpose it was collected.
- Data must be kept secure.
- Data must be processed in accordance with people’s rights.
- Data must not be transferred outside of the EU without adequate protection // to other countries who do not have equivalent data protection laws.
What penalties do you face if you do not follow this law?
- A fine – up to £500k under the DPA 1998 (it is now £17.5m or 4% of annual global turnover, whichever is biggest, under the DPA 2018).
- Prison sentences for intentionally breaching it.
Computer Misuse
Computer Misuse
Topic 8: Legislation & Wider Issues
(2) Computer Misuse Act 1990
Why was this law setup?
This was set up to stop crimes involving computers taking place. Around the time it was setup, there were no laws that stopped crimes taking place electronically.
Why was it setup?
It was setup in 1990 when the internet and computer use started to increase. This meant that computer related crimes started to increase and there were no laws in place to make them illegal.
What does this law make illegal?
| What is illegal? | Example |
|---|---|
| Unauthorised access to a computer system. | Hacking. |
| Unauthorised access to digital materials with the intent to commit further crime. | Planting a virus or other malware. |
| Unauthorised modification of data. | Changing or deleting files you are not permitted to. |
| Making, supplying or obtaining tools used to commit computer misuse offences. | Creating a virus to carry out crime or obtaining key logging software to record usernames and passwords. |
What are the penalties you face if you do not follow this law?
- An unlimited fine.
- Up to 10 years in prison.
Craig n Dave Video
Copyright
Copyright
Topic 8: Legislation & Wider Issues
(3) Copyright Designs and Patents Act 1988
Why was this law setup?
This law protects the owner of a creative work from having it used/distributed without permission. It allows the copyright holder to be credited for their work and the right to control how their work is used.
What does this law cover?
Any creative work, such as:
- Music
- Books
- Videos
- Games
- Software
What does this law make illegal?
Using, copying, modifying or distributing the creative work without permission.
Describe how this law applies to music?
- Copyright assigned to the owner of the music automatically on creation.
- Makes it illegal to copy/distribute the music without permission.
- Copyright holder can ask for their work to be removed from the streaming platform.
- The copyright holder gives a license to people who want to listen to the music.
- This license may restrict their use (e.g. to whom it is played to or the geographical location where it can be accessed).
What are the penalties you could face for not following this law?
- Unlimited fine
- Prison sentence of up to 10 years.
Craig n Dave Video
RIPA
RIPA
Topic 8: Legislation & Wider Issues
(4) Regulation of Investigatory Powers Act 2000.
Why was this law setup?
This allows certain bodies such as Government bodies or the police, the right to monitor communications and internet activities. Its purpose is to detect crime. The law was set up due to criminals increasingly using technology to communicate and coordinate their actions.
What powers does this law give to government bodies?
- They can demand that Internet Service Providers (ISPs) provide access to customer communications.
- They can prevent the existence of interception activities being revealed in court
- It allows for mass surveillance of communications
- Allows the monitoring of an individual’s internet activities
- Demand that access is granted to protection information (e.g. encrypted data).
- Demand that ISPs or businesses install equipment that facilitate surveillance.
What communications can be monitored under this law?
- Emails sent and received
- Communications within chat rooms or instant messaging
- Activity on social networks
- Websites visited
- Listening to telephone conversations
- Intercepting items in the post
What are the concerns surrounding RIPA?
- Some people feel that this law is an invasion of privacy. People have the right to privacy. Generally, people don’t like to be monitored, even if they have nothing to hide.
- Freedom of speech is the right to seek, receive and impart information and ideas of all kinds, by any means. This law can also impact on freedom of speech.
Craig n Dave Video
Social, Cultural, Ethical and Moral Issues
Social, Cultural, Ethical and Moral Issues
Topic 8: Legislation & Wider Issues
(5) Social, Cultural, Ethical and Moral Issues
What is meant by the term moral or ethical issue?
These are issues that about whether something is right and wrong.
What is meant by a social issue?
These are issues that affect many people living in one area or country.
What is meant by a cultural issue?
These are issues about how different groups of people with particular beliefs, practices or languages may be affected by issues.
What is meant by a privacy issue?
People have the right to seclude themselves or information about themselves. A privacy issue is how much of this is impacted on.
Computers in the Workplace
Watch from the beginning until 2:44.
Automated Decision Making
Watch this video from 2:44.
Artificial Intelligence
Watch this video from the beginning until 7:26.
Environmental impacts
Watch this video from 7:26.
Censorship and the Internet
Watch this video from the beginning until 3:30.
Monitoring Behaviour
Watch this video from 3:30.
Analysing Personal Information
Watch this video in full.
Privacy and Offensive Communications
Watch this video from the beginning until 3:36.
Layout, Colour Paradigms and Character Sets
Watch this video from 3:36.